Introduction
This writeup details the exploitation of the "Artificial" machine from Hack The Box,
which showcases interesting vectors involving AI model manipulation and service
exploitation.
Initial Enumeration
First, let's start with a comprehensive port scan using RustScan to identify
available services:
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| | | __ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| _ |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: http://discord.skerritt.blog :
: https://github.com/RustScan/RustScan :-------------------------------------
The config file is expected to be at "/root/.rustscan.toml"
Automatically increasing ulimit value to 10000.
! File limit is lower than default batch size. Consider upping with --ulimit. Ma
y cause harm to sensitive servers
Open 10.10.xx.xx:22
Open 10.10.xx.xx:80
Starting Script(s)
Running script "nmap -vvv -p {{port}} -{{ipversion}} {{ip}} A Pn" on ip 1
0.10.xx.xx
Depending on the complexity of the script, results may take some time to app
ear.
[~] Starting Nmap 7.95 https://nmap.org ) at 2025-06-22 14:34 +08
NSE Loaded 157 scripts for scanning.
NSE Script Pre-scanning.
NSE Starting runlevel 1 (of 3 scan.
Initiating NSE at 1434
Completed NSE at 1434, 0.00s elapsed
NSE Starting runlevel 2 (of 3 scan.
Initiating NSE at 1434
Completed NSE at 1434, 0.00s elapsed
NSE Starting runlevel 3 (of 3 scan.
Initiating NSE at 1434
Completed NSE at 1434, 0.00s elapsed
Initiating SYN Stealth Scan at 1434
Scanning artificial.htb 10.10.xx.xx) [2 ports]
Discovered open port 22/tcp on 10.10.xx.xx
Discovered open port 80/tcp on 10.10.xx.xx
Completed SYN Stealth Scan at 1434, 0.18s elapsed 2 total ports)
Initiating Service scan at 1434
Scanning 2 services on artificial.htb 10.10.xx.xx)
Completed Service scan at 1434, 6.23s elapsed 2 services on 1 host)
Initiating OS detection (try #1 against artificial.htb 10.10.xx.xx)
Initiating Traceroute at 1434
Completed Traceroute at 1434, 0.17s elapsed
Initiating Parallel DNS resolution of 1 host. at 1434
Completed Parallel DNS resolution of 1 host. at 1434, 0.01s elapsed
DNS resolution of 1 IPs took 0.01s. Mode: Async [# 1, OK 0, NX 1, DR 0, SF
0, TR 1, CN 0
NSE Script scanning 10.10.xx.xx.
NSE Starting runlevel 1 (of 3 scan.
Initiating NSE at 1434
Completed NSE at 1434, 4.89s elapsed
NSE Starting runlevel 2 (of 3 scan.
Initiating NSE at 1434
Completed NSE at 1434, 0.57s elapsed
NSE Starting runlevel 3 (of 3 scan.
Initiating NSE at 1434
Completed NSE at 1434, 0.00s elapsed
Nmap scan report for artificial.htb 10.10.xx.xx)
Host is up, received user-set 0.13s latency).
Scanned at 20250622 143415 08 for 14s
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 8.2p1 Ubuntu 4ubuntu0.13 Ubunt
u Linux; protocol 2.0
| ssh-hostkey:
| 3072 7c:e48d:84:c5:de:913a:5a:2b:9d:34:ed:d69917 RSA
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDNABz8gRtjOqG4+jUCJb2
NFlaw1auQlaXe1/IBhqrriREBnu476PNw6mFG9ifT57WWE/qvAZQFYRvPupR
eMJD4C3bE3fSLbXAoP037JrZkNmPRpVetRjUwP1acu7golA8MnPGzGa2UW
38oK/TnkJDlZgRpQq/7DswCr38IPxvHNO/15iizgOETTTEU8pMtUm/ISNQfPcG
LGc0x5hWxCPbu75OOOsPt2vA2qD4/sb9bDCOR57bAt4i+WEqp7Ri/act+f4k6v
ypm1sebNXeYaKapw+W83en2LnJOU0lsdhJiAPKaD/srZRZKOR0bsPcKOqLWQ
R/A6Yy3iRE8fcKXzfbhYbLUiXZzuUJoEMW33l8uHuAza57PdiMFnKqLQ6LBfw
Ys64Q3v8oAn5O7upCI/nDQ6raclTSigAKpPbliaL0HE/P7UhNacrGE7Gsk/FwADi
XgEAseTn609wBnLzXyhLzLb4UVu9yFRWITkYQ6vq4ZqsiEnAsur/jt8WZY6MQ
8
| 256 83462d:cf:736d:286f:11:d51d:b48820:d67c ECDSA
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdH
AyNTYAAABBBOdlb8oU9PsHX8FEPY7DijTkQzsjeFKFf/xgsEav4qedwBUFzOet
bfQNn3ZrQ9PMIHrguBG+cXlA2gtzK4NPohU
| 256 e3182e:3b:4061:b45987:e84a:29240f:6a:fc ED25519
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIH8QL1LMgQkZcpxuylBjhjosiCx
cStKt8xOBU0TjCNmD
80/tcp open http syn-ack ttl 63 nginx 1.18.0 Ubuntu)
| http-methods:
|_ Supported Methods: HEAD OPTIONS GET
|_http-title: Artificial AI Solutions
|_http-server-header: nginx/1.18.0 Ubuntu)
Warning: OSScan results may be unreliable because we could not find at least
1 open and 1 closed port
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 5.19
TCP/IP fingerprint:
OSSCANV7.95%E4%D6/22%OT22%CT%CU40924%PVY%DS
2%DCT%GN%TM6857A3F5
OS%P=x86_64-pc-linux-gnu)SEQ(SPFE%GCD1%ISR107%TIZ%CIZ%II
=I%TSAOPSO
OS1M542ST11NW7%O2M542ST11NW7%O3M542NNT11NW7%O4M54
2ST11NW7%O5M542ST11N
OSW7%O6M542ST11WINW1FE88%W2FE88%W3FE88%W4FE88%
W5FE88%W6FE88ECNR
OSY%DFY%T40%WFAF0%OM542NNSNW7%CCY%QT1RY%DF
Y%T40%SO%AS%FAS%
OSRD0%QT2RNT3RNT4RY%DFY%T40%W0%SA%AZ%F
=R%O%RD0%QT5RY
OS%DFY%T40%W0%SZ%AS%FAR%O%RD0%QT6RY%DF
Y%T40%W0%SA%AZ%FR
OS%O%RD0%QT7RY%DFY%T40%W0%SZ%AS%FAR%O
=%RD0%QU1RY%DFN%T
OS40%IPL164%UN0%RIPLG%RIDG%RIPCKG%RUCKG%RUDGIE
(RY%DFIN%T40%CDS
OS
Uptime guess: 19.549 days (since Tue Jun 3 012417 2025
Network Distance: 2 hops
TCP Sequence Prediction: Difficulty=254 Good luck!
IP ID Sequence Generation: All zeros
Service Info: OS Linux; CPE cpe:/o:linux:linux_kernel
TRACEROUTE (using port 22/tcp)
HOP RTT ADDRESS
1 165.32 ms 10.10.16.1
2 79.75 ms artificial.htb 10.10.xx.xx)
NSE Script Post-scanning.
NSE Starting runlevel 1 (of 3 scan.
Initiating NSE at 1434
Completed NSE at 1434, 0.00s elapsed
NSE Starting runlevel 2 (of 3 scan.
Initiating NSE at 1434
Completed NSE at 1434, 0.00s elapsed
NSE Starting runlevel 3 (of 3 scan.
Initiating NSE at 1434
Completed NSE at 1434, 0.00s elapsed
Read data files from: /usr/share/nmap
OS and Service detection performed. Please report any incorrect results at htt
ps://nmap.org/submit/ .
Nmap done: 1 IP address 1 host up) scanned in 14.47 seconds
Raw packets sent: 34 2.306KB | Rcvd: 22 3.270KB
┌──(root
㉿
kali)-[~]
└─# echo "10.10.xx.xx artificial.htb" | tee -a /etc/hosts10.10.xx.xx artificial.htb
Web Application Exploration
After adding the hostname to our
/etc/hosts file, we can access the web application.
Upon initial inspection, we discover a registration functionality that allows new
users to create accounts.
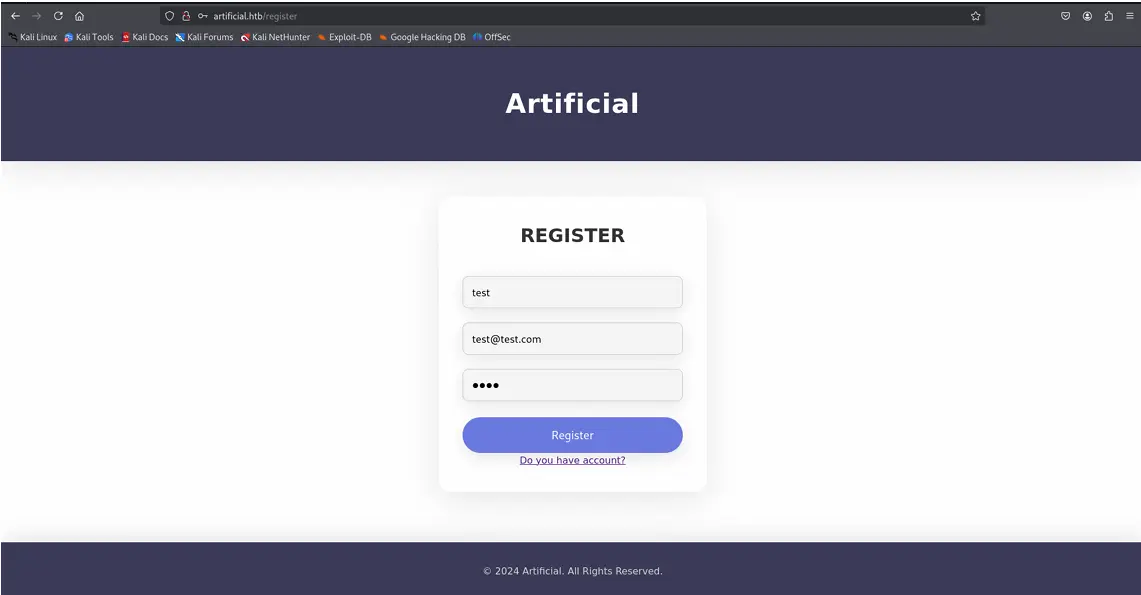
Once that lets login and here we have a file upload functionality.
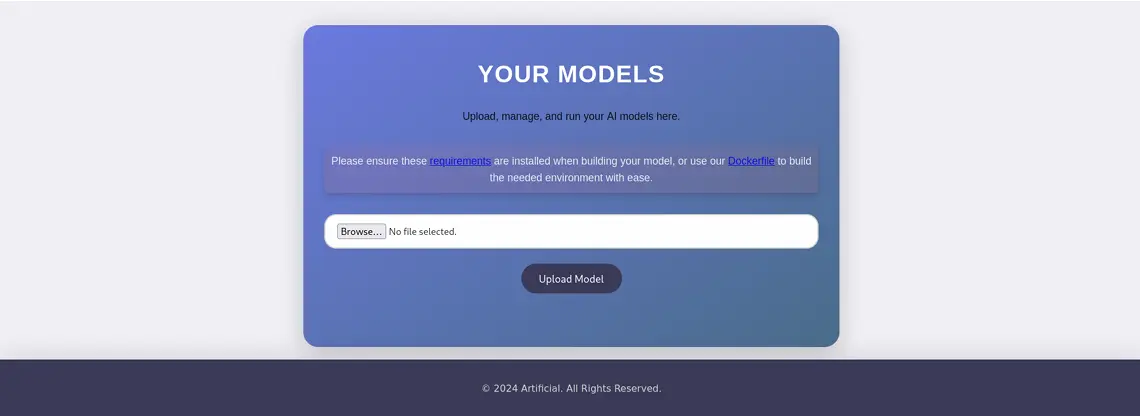
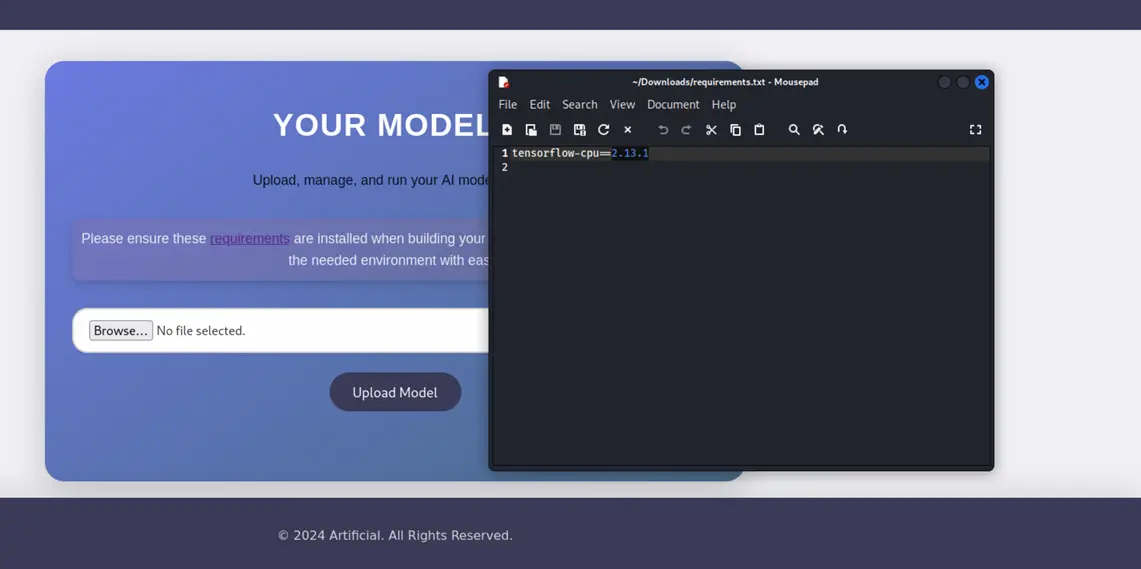
Initial Foothold: TensorFlow Model Exploitation
After analyzing the application's functionality, I discovered it accepts model
uploads. This presented an interesting attack vector through TensorFlow model
manipulation. Based on research from
TensorFlow Remote Code Execution with Malicious Model, I crafted the following exploit:
