Hack The Box: Puppy Writeup (Medium) - Season 8
This HTB writeup details the process of compromising the Hack The Box machine "Puppy," leading to full root access. This machine presented a realistic Active Directory environment requiring careful enumeration and leveraging found credentials. We are presented with following information- "As is common in real life pentests, you will start the Puppy box with credentials for the following account: levi.james / KingofAkron2025!"

Challenge: Puppy
OS: Windows
Difficulty: Medium
Points: 30
Initial Foothold
The challenge began with provided credentials for a low-privileged user account, levi.james. We started by enumerating the services running on the target machine, identified as a Windows host, likely a Domain Controller for the PUPPY.HTB domain.
Initial Nmap scan revealed standard Active Directory ports like 53 (DNS), 88 (Kerberos), 135 (MSRPC), 139 (NetBIOS SSN), 389 (LDAP), 445 (SMB), 636 (LDAPS), and 5985 (WinRM), confirming the target's role.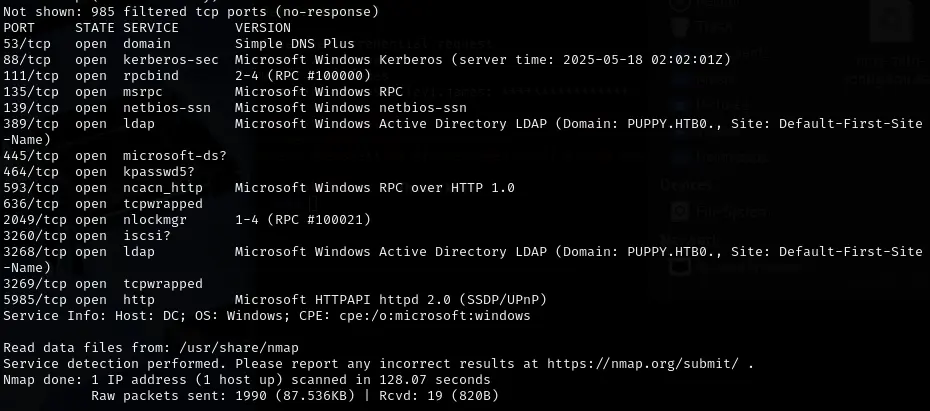
Using the initial levi.james credentials, we explored the available network services, focusing on SMB (Server Message Block). Port 139 is used for older SMB versions that rely on NetBIOS over TCP/IP, while Port 445 is used for newer SMB versions that operate directly over TCP/IP without requiring NetBIOS.
Enumeration and Credential Discovery
Enumerating the accessible SMB shares using smbclient with the initial credentials revealed several shares, including SYSVOL, NETLOGON, ADMIN$, C$, IPC$, and an interesting share named DEV ("DEV-SHARE for PUPPY-DEVS").
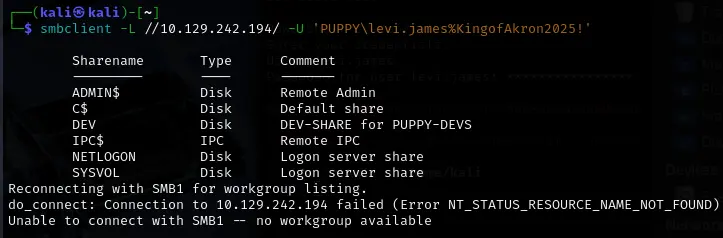
┌──(kali㉿kali)-[~]
└─$ smbclient //<IP>/DEV -U 'PUPPY\levi.james%KingofAkron2025!'
Try "help" to get a list of possible commands.
smb: \> list
0: server=10.129.242.194, share=DEV
smb: \> ls
NT_STATUS_ACCESS_DENIED listing \*
smb: \> exit
