This write-up walks you through the TryHackMe room Industrial Intrusion. You can join the room here.
Challenge Overview
The challenge presents us with a lock-like image and the IP address of the target machine.
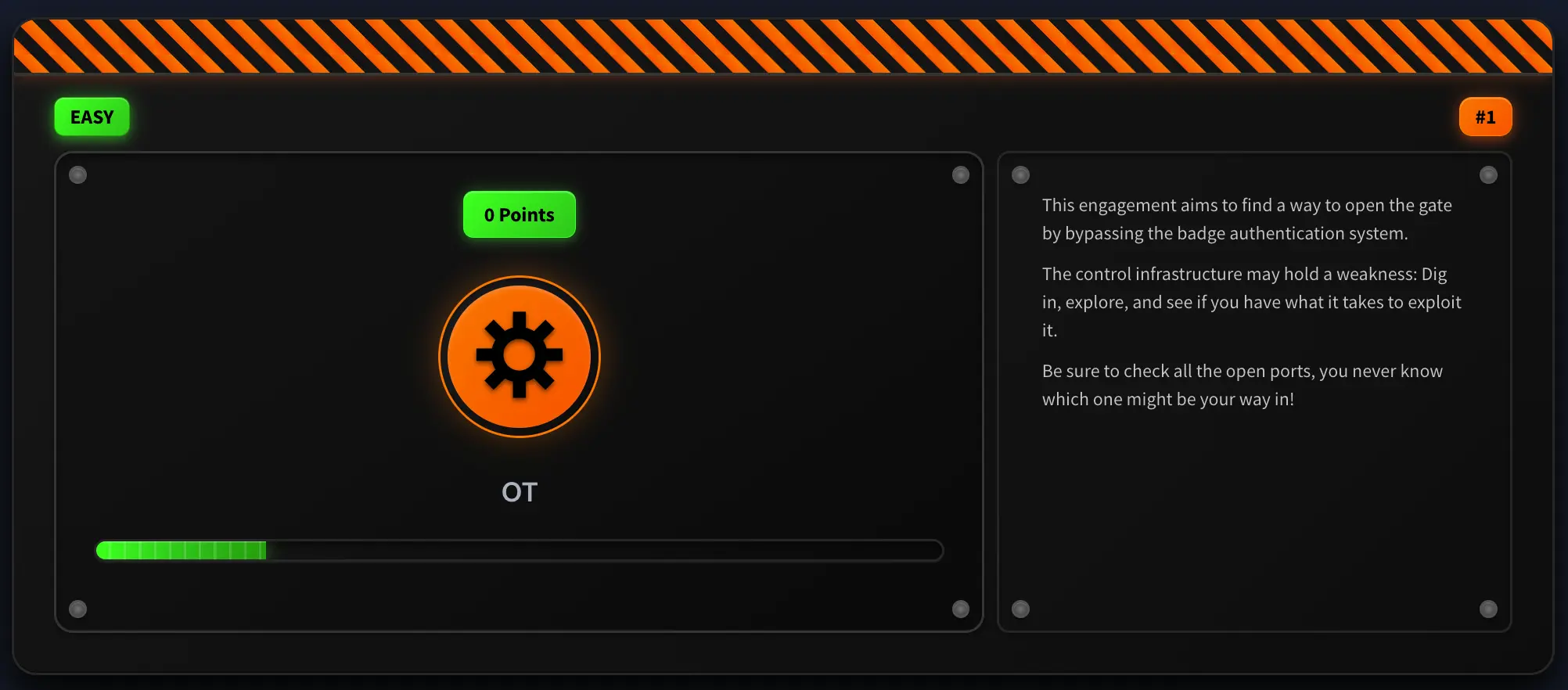
From what I gathered, the main objective is to exploit a vulnerability in the control infrastructure and bypass the badge-based authentication system.
Initial Foothold
Port Scanning
As the description mentions: “Be sure to check all the open ports” So, naturally, I started with a nmap scan:
nmap -p0- -v -A -T4 { target_IP }
Scan Result:
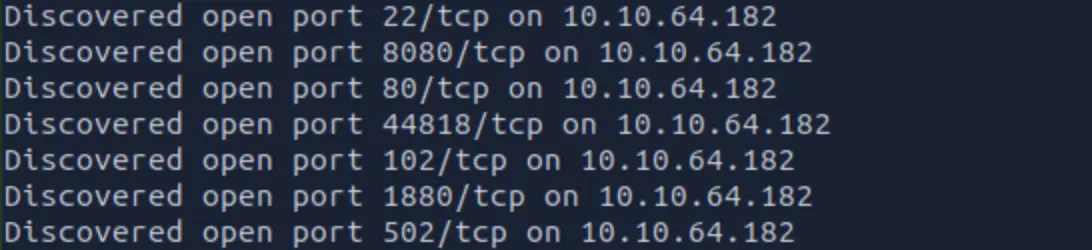
I found 7 open ports. After a bit of research, here’s what I got:
| Port | Common Service | Context |
|---|---|---|
| 22 | SSH | Secure remote shell |
| 80 | HTTP | Standard web server |
| 8080 | HTTP Alt / App Server | Proxy, dev/testing, web apps |
| 502 | Modbus/TCP | Industrial automation |
| 102 | Siemens S7 | PLC communications |
| 1880 | Node‑RED / MQTT variant | IoT flow programming / messaging |
| 44818 | EtherNet/IP | Industrial control networking |
These are all typical in an OT setup, and the room’s description clearly points us in that direction.
Website Recon
I explored each open port to gather more details.
On port 80, I found a webpage titled “Gate Monitor” showing the status of a door, which is currently closed. This ties in with the challenge hint about badge-based auth.
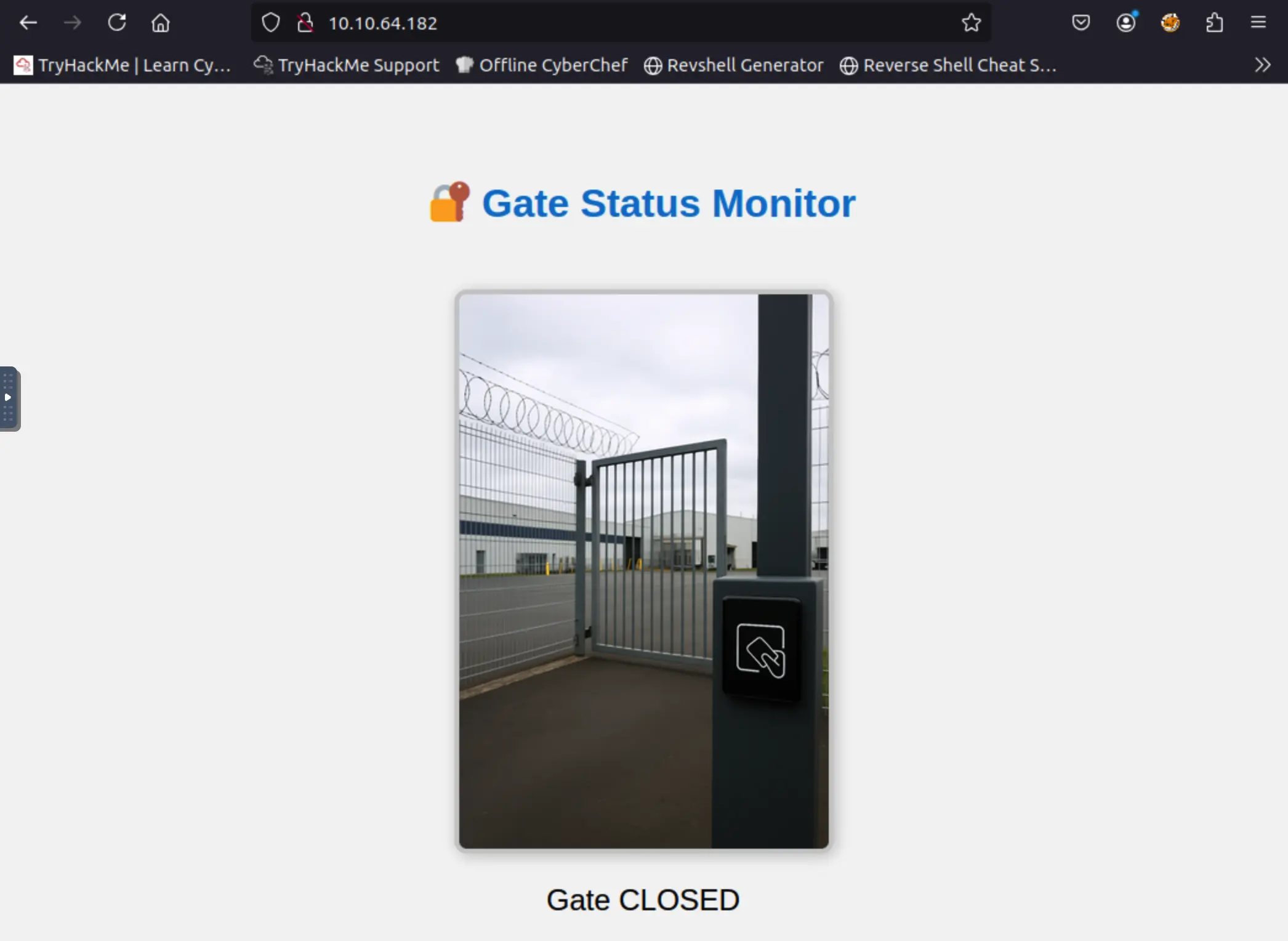
Clicking the door image didn’t do anything, and the page source didn’t reveal anything useful either.
Port 8080 hosted a basic OpenPLC login page.
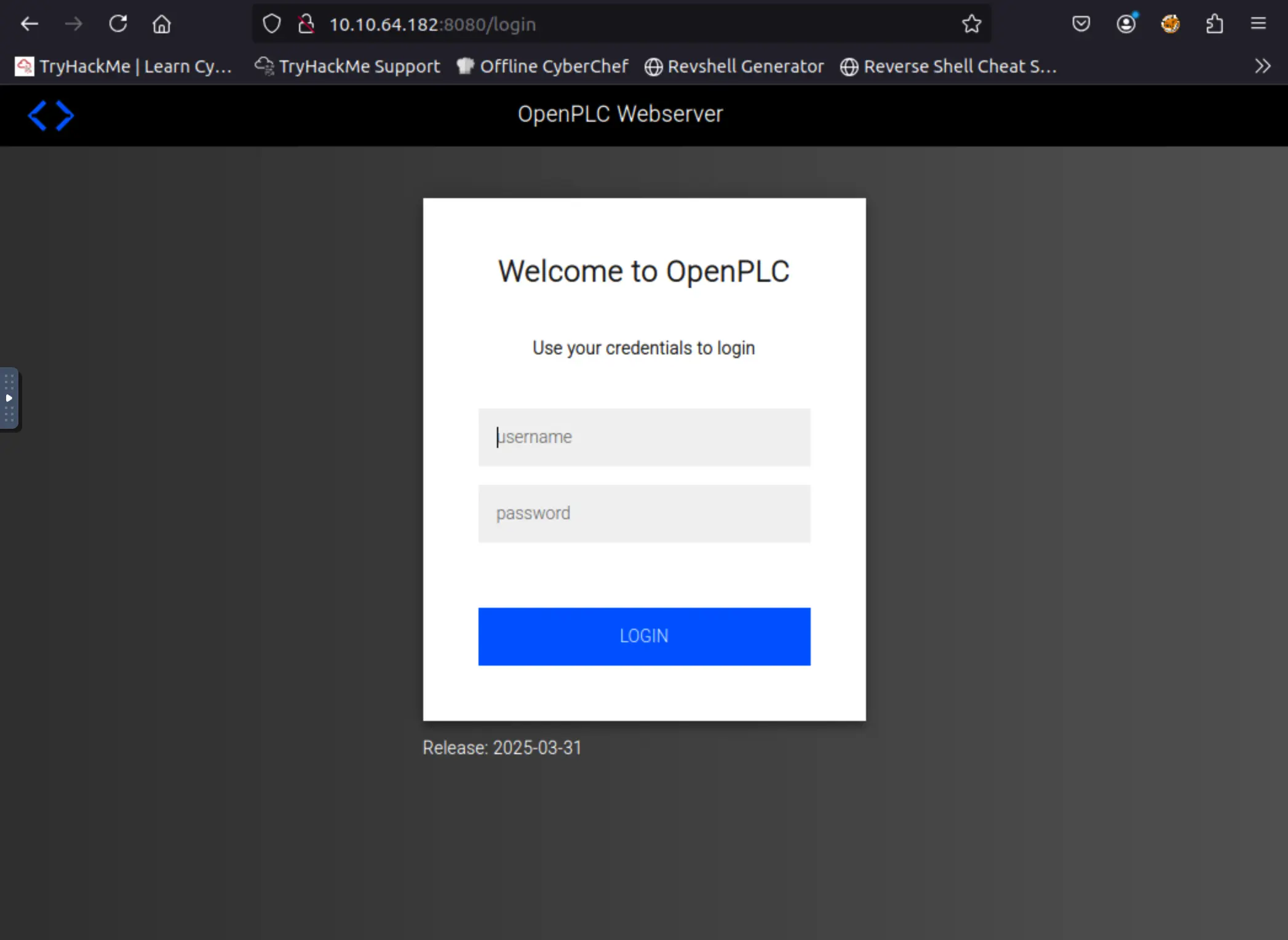
Tried poking around a bit here, but didn’t have valid credentials. Also attempted to work with Modbus/TCP, but… yeah, that didn’t go so well.
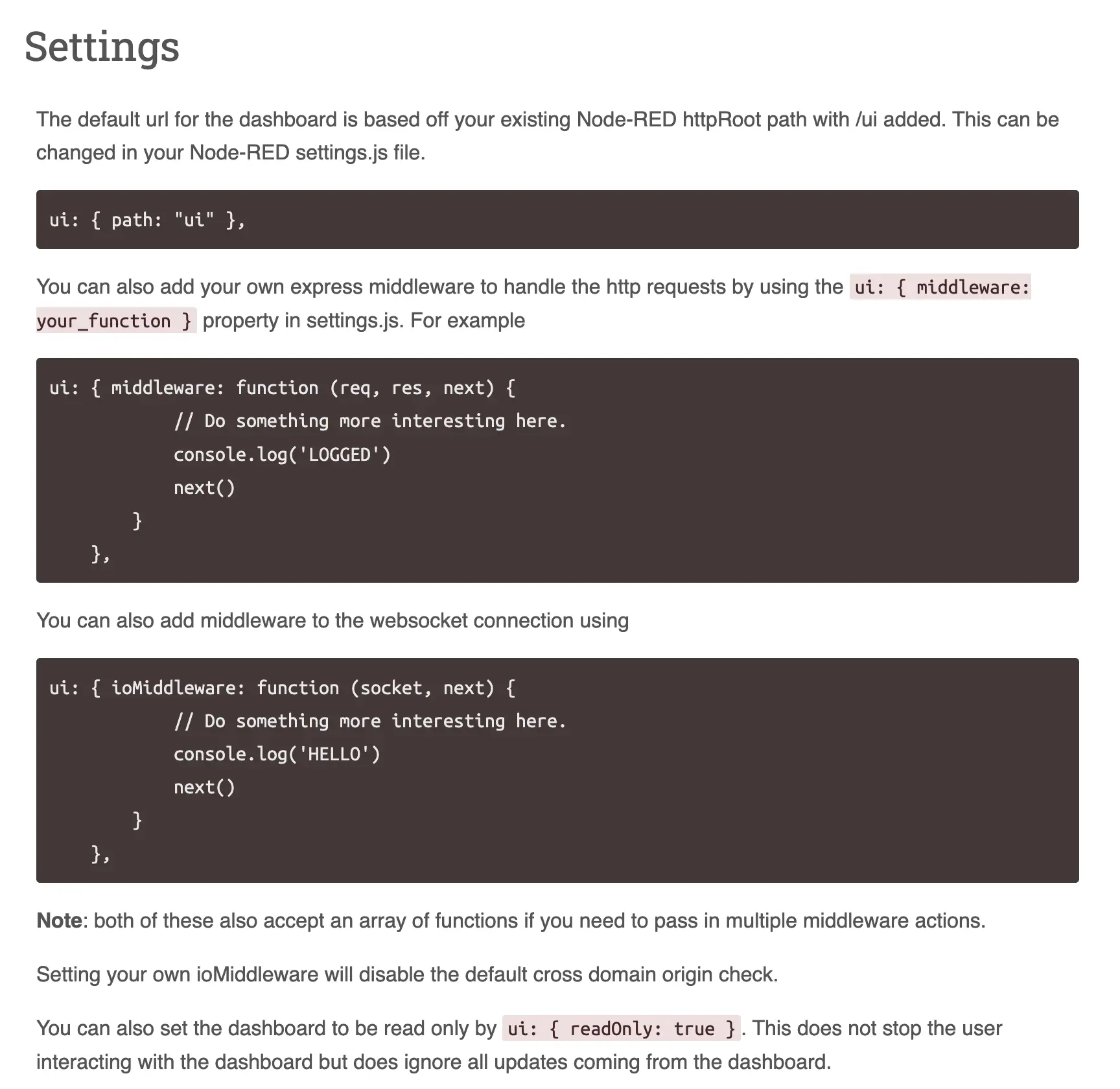
Next up, I checked port 1880, which was running Node-RED. I wasn’t super familiar with it, so I skimmed through the Node-RED documentation.
Finding Vulnerability
In the configuration settings section, I learned that by default, Node-RED exposes a /ui endpoint, which can be a potential security hole if left unauthenticated. That was promising!